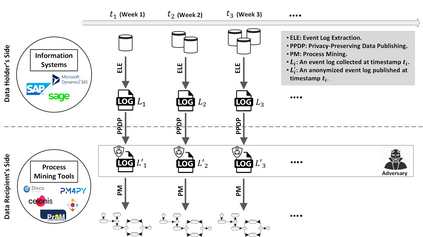
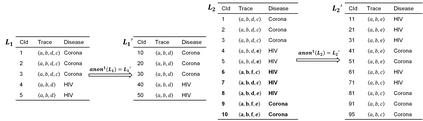
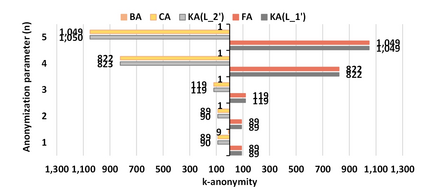
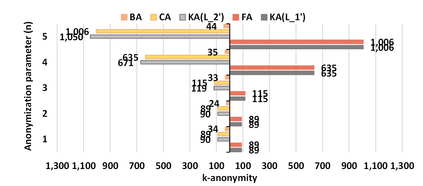
Process mining enables organizations to discover and analyze their actual processes using event data. Event data can be extracted from any information system supporting operational processes, e.g., SAP. Whereas the data inside such systems is protected using access control mechanisms, the extracted event data contain sensitive information that needs to be protected. This creates a new risk and a possible inhibitor for applying process mining. Therefore, privacy issues in process mining become increasingly important. Several privacy preservation techniques have been introduced to mitigate possible attacks against static event data published only once. However, to keep the process mining results up-to-date, event data need to be published continuously. For example, a new log is created at the end of each week. In this paper, we elaborate on the attacks which can be launched against continuously publishing anonymized event data by comparing different releases, so-called correspondence attacks. Particularly, we focus on group-based privacy preservation techniques and show that provided privacy requirements can be degraded exploiting correspondence attacks. We apply the continuous event data publishing scenario to existing real-life event logs and report the anonymity indicators before and after launching the attacks.
翻译:开采过程使各组织能够利用事件数据发现和分析其实际过程。从任何支持操作过程的信息系统(例如SAP)中可以提取事件数据。这些系统中的数据是使用出入控制机制受到保护的,而提取的事件数据则含有需要保护的敏感信息。这造成了新的风险,并可能抑制了开采过程的应用。因此,采矿过程中的隐私问题变得越来越重要。引入了几种隐私保护技术,以减轻对静态事件数据可能发生的攻击。然而,为了不断更新采矿结果,事件数据需要不断公布。例如,在每星期结束时创建一份新的日志。在本文件中,我们详细阐述了通过比较不同排放物、所谓的通信攻击,可以针对持续发布匿名事件数据发动的袭击。特别是,我们侧重于基于群体的隐私保护技术,并表明提供隐私要求可以降低利用通信攻击的情况。我们将连续事件数据公布情景应用于现有的真实事件日志,并在发动攻击之前和之后报告匿名指标。
相关内容
Source: Apple - iOS 8