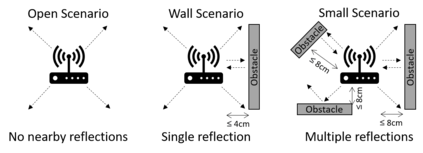
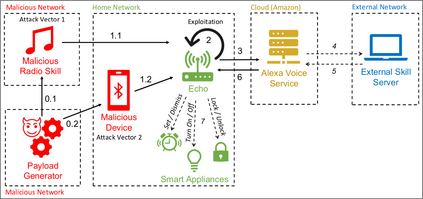
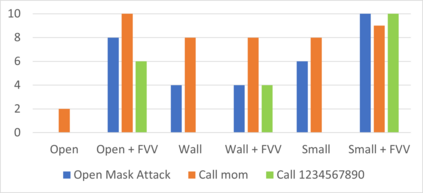
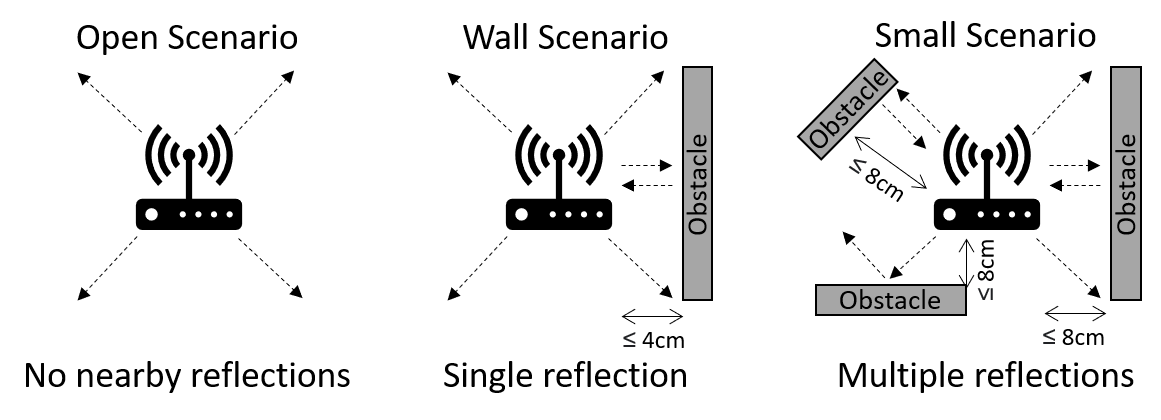
We present Alexa versus Alexa (AvA), a novel attack that leverages audio files containing voice commands and audio reproduction methods in an offensive fashion, to gain control of Amazon Echo devices for a prolonged amount of time. AvA leverages the fact that Alexa running on an Echo device correctly interprets voice commands originated from audio files even when they are played by the device itself -- i.e., it leverages a command self-issue vulnerability. Hence, AvA removes the necessity of having a rogue speaker in proximity of the victim's Echo, a constraint that many attacks share. With AvA, an attacker can self-issue any permissible command to Echo, controlling it on behalf of the legitimate user. We have verified that, via AvA, attackers can control smart appliances within the household, buy unwanted items, tamper linked calendars and eavesdrop on the user. We also discovered two additional Echo vulnerabilities, which we call Full Volume and Break Tag Chain. The Full Volume increases the self-issue command recognition rate, by doubling it on average, hence allowing attackers to perform additional self-issue commands. Break Tag Chain increases the time a skill can run without user interaction, from eight seconds to more than one hour, hence enabling attackers to setup realistic social engineering scenarios. By exploiting these vulnerabilities, the adversary can self-issue commands that are correctly executed 99% of the times and can keep control of the device for a prolonged amount of time. We reported these vulnerabilities to Amazon via their vulnerability research program, who rated them with a Medium severity score. Finally, to assess limitations of AvA on a larger scale, we provide the results of a survey performed on a study group of 18 users, and we show that most of the limitations against AvA are hardly used in practice.
翻译:Alexa 与 Alexa (AvA) 相比(AvA),我们展示了Alexa 与 Alexa (AvA), 这是一种新式袭击, 利用含有语音指令和音效复制方法的音频文件, 以攻击性的方式利用包含声音指令和音频复制方法的音频文件, 来控制亚马逊回声设备。 AvA 利用一个事实, Alexa运行在回音设备上正确解读音频文件, 即使是由音频设备本身播放, 也利用了命令自我脆弱性。 因此, AvA 消除了让一个无赖的语者接近受害者回声回声系统(AvA) 的必要性, 使许多攻击者都受到同样的限制。 AvAA, 攻击者可以自我发布任何允许的指令, 代表合法用户控制回回音设备。 我们已经核实, Alexa 攻击者可以控制家里智能的智能设备, 购买不想要的东西, 修改日历 日历 日历