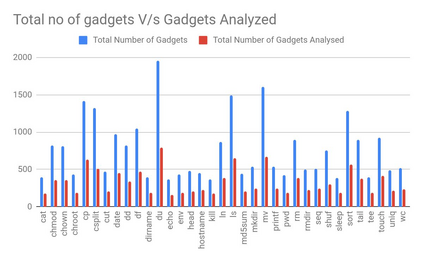
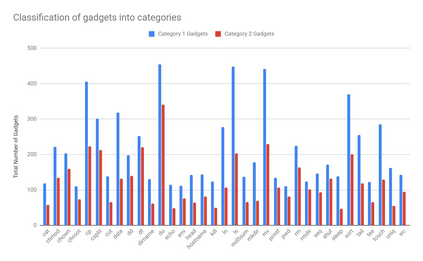
Control Flow Hijacking attacks have posed a serious threat to the security of applications for a long time where an attacker can damage the control Flow Integrity of the program and execute arbitrary code. These attacks can be performed by injecting code in the program's memory or reusing already existing code in the program (also known as Code-Reuse Attacks). Code-Reuse Attacks in the form of Return-into-libc Attacks or Return-Oriented Programming Attacks are said to be Turing Complete, providing a guarantee that there will always exist code segments (also called ROP gadgets) within a binary allowing an attacker to perform any kind of function by building a suitable ROP chain (chain of ROP gadgets). Our goal is to study different techniques of performing ROP Attacks and find the difficulties encountered to perform such attacks. For this purpose, we have designed an automated tool which works on 64-bit systems and generates a ROP chain from ROP gadgets to execute arbitrary system calls.
翻译:控制流动袭击对应用程序的安全构成了长期的严重威胁,攻击者可以破坏程序控制流程的完整性并任意执行代码。这些袭击可以通过在程序记忆中注入代码或重新使用程序中已有代码(又称代码-再使用袭击)来实施。 以返回到图书馆袭击或返回方向的方案编制袭击为形式的代码再次使用袭击据说是Turing 完成,提供保证在二进制中始终存在代码部分(也称为 ROP 工具),允许攻击者通过建立合适的 ROP 链( ROP 工具链)来履行任何功能。 我们的目标是研究实施 ROP 袭击的不同技术,并找出实施此类袭击时遇到的困难。 为此,我们设计了一个自动工具,在64位系统上运行,并生成了来自 ROP 工具的 ROP 链,用于执行任意的系统呼叫。