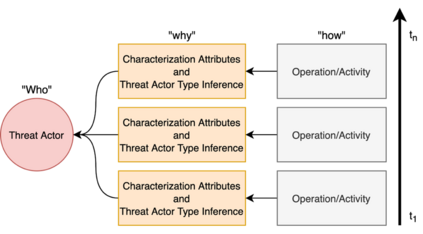
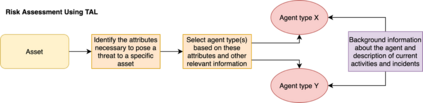
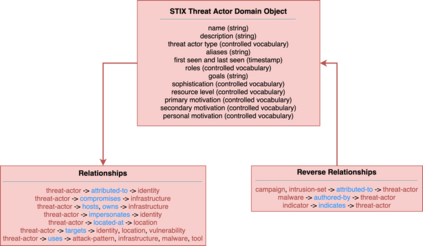
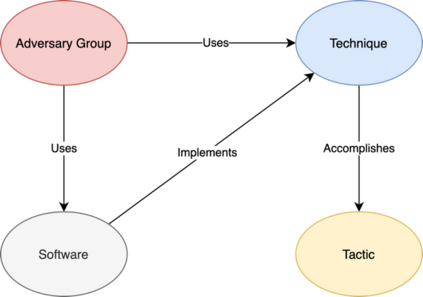
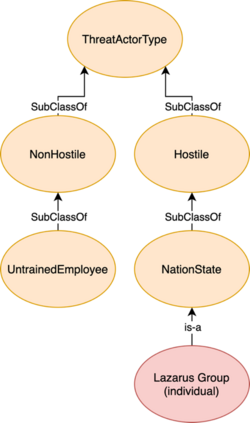
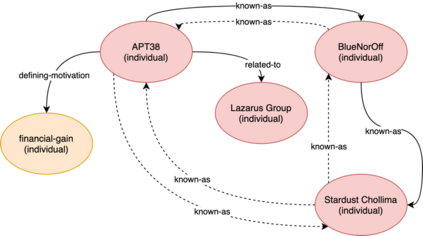
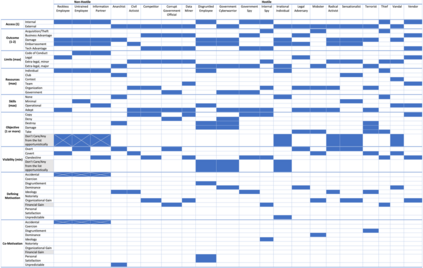
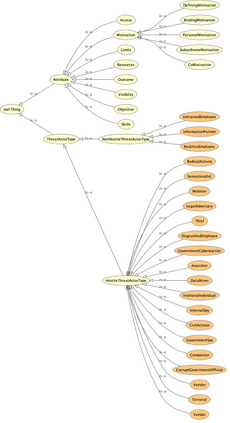
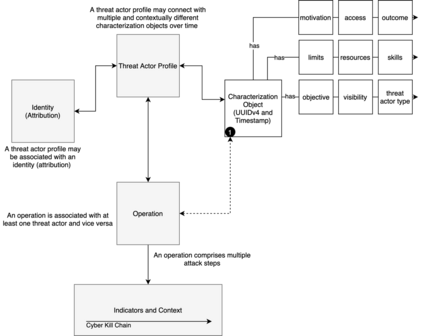
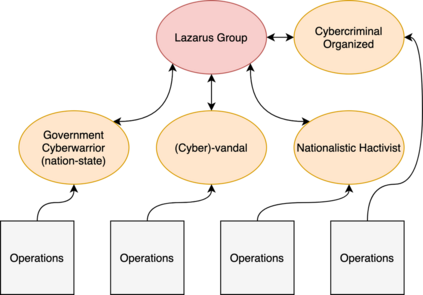
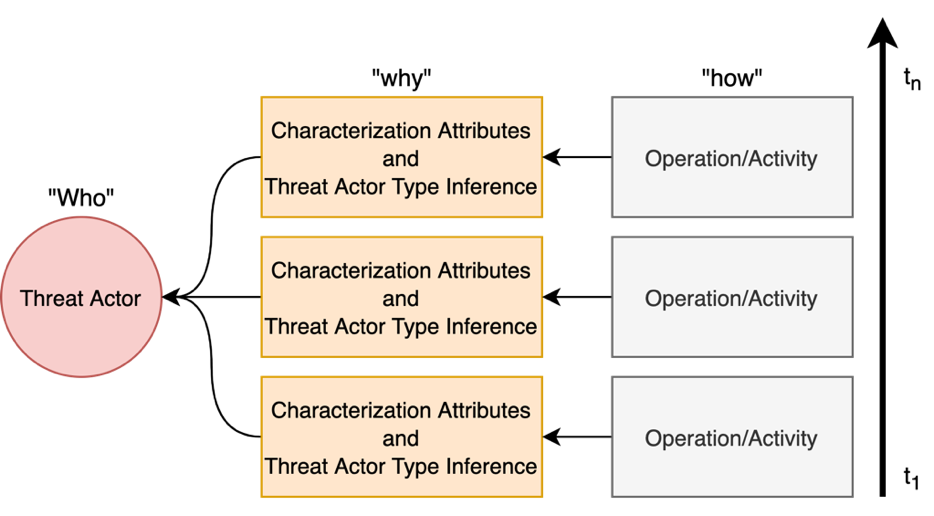
As the cyber threat landscape is constantly becoming increasingly complex and polymorphic, the more critical it becomes to understand the enemy and its modus operandi for anticipatory threat reduction. Even though the cyber security community has developed a certain maturity in describing and sharing technical indicators for informing defense components, we still struggle with non-uniform, unstructured, and ambiguous higher-level information, such as the threat actor context, thereby limiting our ability to correlate with different sources to derive more contextual, accurate, and relevant intelligence. We see the need to overcome this limitation in order to increase our ability to produce and better operationalize cyber threat intelligence. Our research demonstrates how commonly agreed upon controlled vocabularies for characterizing threat actors and their operations can be used to enrich cyber threat intelligence and infer new information at a higher contextual level that is explicable and queryable. In particular, we present an ontological approach to automatically inferring the types of threat actors based on their personas, understanding their nature, and capturing polymorphism and changes in their behavior and characteristics over time. Such an approach not only enables interoperability by providing a structured way and means for sharing highly contextual cyber threat intelligence but also derives new information at machine speed and minimizes cognitive biases that manual classification approaches entail.
翻译:随着网络威胁景观不断变得日益复杂和多变,理解敌人及其预测性减少威胁的操作方式变得更加关键。尽管网络安全界在描述和分享用于通报国防组成部分的技术指标方面已经发展到一定成熟程度,但我们仍然在与非统一、非结构化和模棱两可的更高层次的信息,例如威胁行为体的背景进行斗争,从而限制我们与不同来源建立联系的能力,从而获得更符合背景、准确和相关的情报。我们认为需要克服这一限制,以便提高我们制作和更好地操作网络威胁情报的能力。我们的研究表明,如何利用共同商定的用于确定威胁行为体特征及其行动的受控词汇来丰富网络威胁情报,并在更高层次上推导出可解释和可查询的新信息。特别是,我们提出了一个理论方法,自动推断基于其个人特征、了解其性质、捕捉其行为和特性的多种形态和变化的各种威胁行为体。这种方法不仅能够通过提供结构化的方式和手段来分享高度背景化的网络威胁信息,而且还能带来新的系统化。