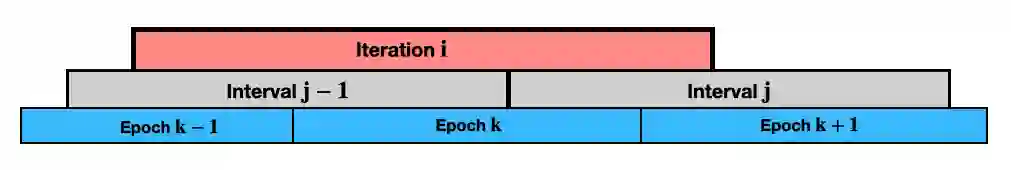
A Sybil attack occurs when an adversary pretends to be multiple identities (IDs). Limiting the number of Sybil (bad) IDs to a minority permits the use of well-established tools for tolerating malicious behavior, such as protocols for Byzantine consensus and secure multiparty computation. A popular technique for enforcing this minority is resource burning; that is, the verifiable consumption of a network resource, such as computational power, bandwidth, or memory. Unfortunately, prior defenses require non-Sybil (good) IDs to consume at least as many resources as the adversary, unless the rate of churn for good IDs is sufficiently low. Since many systems exhibit high churn, this is a significant barrier to deployment. We present two algorithms that offer useful guarantees against Sybil adversary under a broadly-applicable model of churn. The first is GoodJEst, which estimates the number of good IDs that join the system over any window of time, despite the adversary injecting bad IDs. GoodJEst applies to a broad range of system settings, and we demonstrate its use in our second algorithm, a new Sybil defense called ERGO. Even under high churn, ERGO guarantee (1) there is always a minority of bad IDs in the system; and (2) when the system is under attack, the good IDs burn resources at a total rate that is sublinear in the adversary's consumption. To evaluate the impact of our theoretical results, we investigate the performance of ERGO alongside prior defenses that employ resource burning. Based on our experiments, we design heuristics that further improve the performance of ERGO by up to four orders of magnitude over these previous Sybil defenses.
翻译:当对手假装多重身份(IDs)时,就会发生Sybil攻击。 将 Sybil (bad) ID的数量限制在少数点, 从而允许使用成熟的工具来容忍恶意行为, 如Byzantine共识协议和确保多党计算。 执行这一少数点的流行技术是资源燃烧, 也就是说, 可以核实地消耗网络资源, 如计算能力、 带宽或记忆等。 不幸的是, 先前的防御需要非Sybil ( good) ID 来消费至少与对手一样多的资源, 除非对好ID 的比例足够低。 由于许多系统表现出高度的胆量, 能够使用成熟的工具来容忍恶意行为。 由于许多系统表现出高度的胆量, 这是一个重要的部署障碍。 我们用两种算法来向Sybil 对手提供有用的保证, 在一个广泛适用的模型下, 即GoodJEst, 估计任何时间加入系统的良好身份数据的数量, 尽管有相反的注射错误。 GoodJEst 适用于广泛的系统设置, 并且我们在那里展示了它的用途, 在我们的第二个算法中, 新的Sylbil Defor Defor destrefor deview 需要 一直在 一直 la destrate deal destrate la destration a lades a lades lax lax lax lax lax a lax a lax a la la lax a la la la lax lax lax be lax lax lax a lax lax lax lax lax lax lax lax lax lax lax lax lax lax lax lax lax lax laut lax a lax lax lax lax lax lax lax lax lax lautd lax lax lax lax lax lax lax lax lax lax lax la lax lax lax lax lax lax lax lax lax lax la la