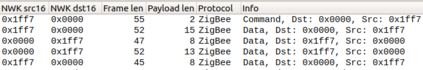
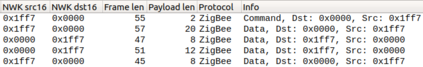
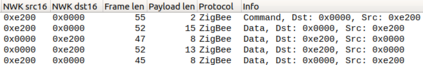
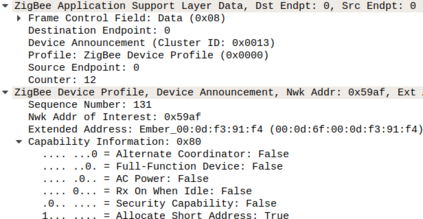
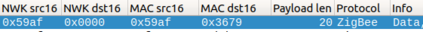
In this work, we analyze the privacy guarantees of Zigbee protocol, an energy-efficient wireless IoT protocol that is increasingly being deployed in smart home settings. Specifically, we devise two passive inference techniques to demonstrate how a passive eavesdropper, located outside the smart home, can reliably identify in-home devices or events from the encrypted wireless Zigbee traffic by 1) inferring a single application layer (APL) command in the event's traffic burst, and 2) exploiting the device's periodic reporting pattern and interval. This enables an attacker to infer user's habits or determine if the smart home is vulnerable to unauthorized entry. We evaluated our techniques on 19 unique Zigbee devices across several categories and 5 popular smart hubs in three different scenarios: i) controlled shield, ii) living smart-home IoT lab, and iii) third-party Zigbee captures. Our results indicate over 85% accuracy in determining events and devices using the command inference approach, without the need of a-priori device signatures, and 99.8% accuracy in determining known devices using the periodic reporting approach. In addition, we identified APL commands in a third party capture file with 90.6% accuracy. Through this work, we highlight the trade-off between designing a low-power, low-cost wireless network and achieving privacy guarantees.
翻译:在这项工作中,我们分析了Zigbee协议的隐私保障,这是一个节能的无线IoT协议,正在越来越多地在智能家庭环境中部署。具体地说,我们设计了两种被动推论技术,以展示位于智能家庭之外的被动窃听器如何可靠地识别来自加密无线Zigbee交通的家用装置或事件:1)在事件交通爆发时推断出单一应用层(APL)命令,2)利用该装置的定期报告模式和间隔。这使得攻击者能够推断用户的习惯或确定智能家庭是否易受未经授权进入的伤害。我们评估了我们在以下三种不同情景中的19个独特的Zigbee装置和5个流行智能中心的技术:一) 控制屏蔽,二) 生活在智能家庭IoT实验室,三) 第三方Zigbee捕捉。我们的结果表明,在使用命令推断方法确定事件和装置时,85%的准确性超过指令,而不需要优先装置签字,99.8%的精确度用于使用低度报告方法确定已知的装置。此外,我们查明了在使用低度网络中实现低度的APL命令的准确度。