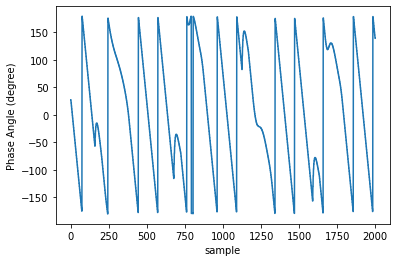
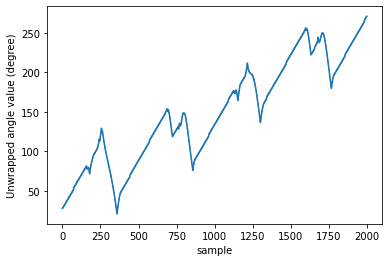
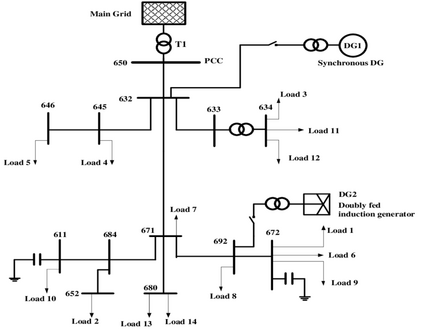
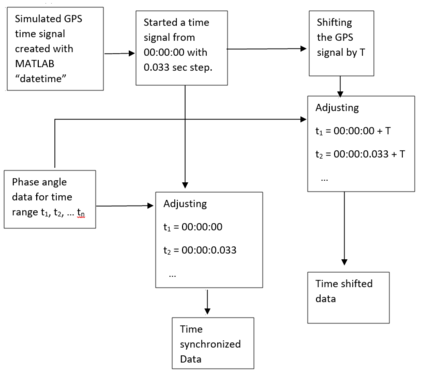
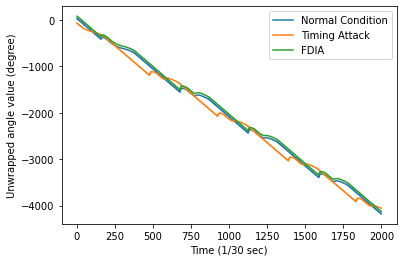
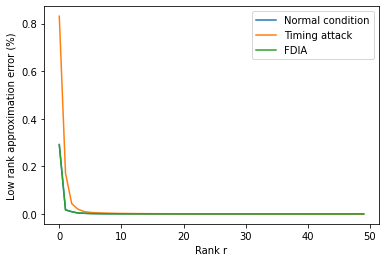
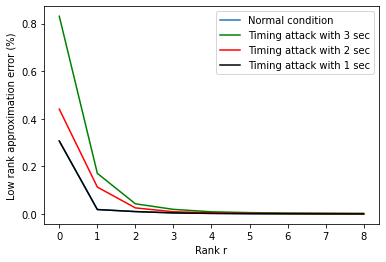
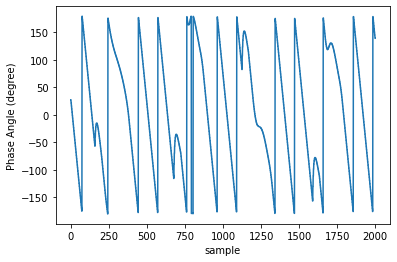
Introduction of PMUs to cyber-physical system pro-vides accurate data acquisition, while posing additional risk of being the victim of cyber attack. Both False Data Injection Attack (FDIA) and GPS-spoofing or timing attack can provide malicious data to the cyber system, though these two attacks require different post-attack contingency plan. Thus accurate detection of timing attack and separating it from conventional FDIA has become a very important research area. In this article, a successful detection of timing attack mechanism is proposed. Firstly, a method to distinguish timing attack and FDIA using unwrapped phase angle data is developed. Secondly, utilizing low rank Henkel matrix property to differentiate timing attack from electrical events is also presented. Finally, an experimental validation of proposed model is performed on IEEE 13 bus system using simulated GPS-spoofing attack. It can be observed that the timing attack can increase the rank 1 approximation error of Henkel matrix of unwrapped angles by 700% for 3 sec delay in GPS time-stamp. The rank 1 approximation error is increased by 500% for 2 sec delay and the increase is insignificant for 1sec delay attack. FDIA doesn't show any significant change in the low rank approximation profile of Henkel matrix.
翻译:引入 PMUs 用于网络物理系统, 有助于获取准确的数据, 同时也增加了成为网络攻击受害者的风险。 假数据输入攻击和GPS投射或定时攻击都可以向网络系统提供恶意数据, 尽管这两起攻击需要不同的攻击后应急计划。 因此,准确检测时间攻击并将其与常规的FDIA分离已成为一个非常重要的研究领域。 在此文章中, 提议成功检测时间攻击机制。 首先, 开发了一种方法, 使用未包装的阶段角度数据区分时间攻击和FDIA。 其次, 使用低级别的 Henkel 矩阵属性来区分时间攻击与电子事件。 最后, 在 IEEEE 13 公共汽车系统中, 使用模拟的GPS Poofing 攻击, 对拟议模式进行了实验性验证。 可以看到, 时间攻击可以使未包装角度的Henkel 矩阵增加700%, 用于全球定位系统时间戳中3秒的延迟。 1级近似误差增加了500%, 用于2秒的延迟, 而1 sec 延迟袭击的配置是微不足道的。 IMFDIGRA 。