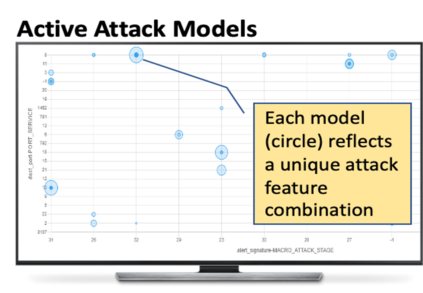
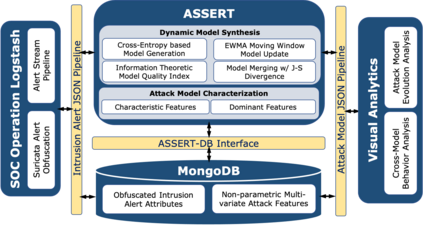
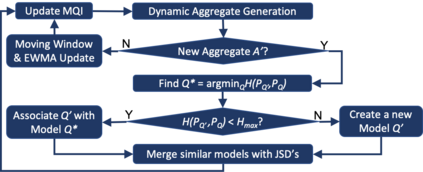
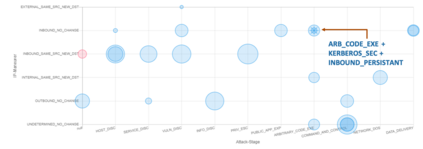
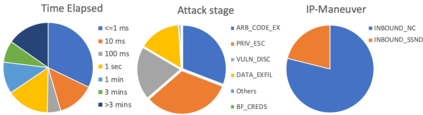
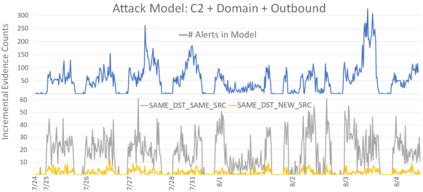
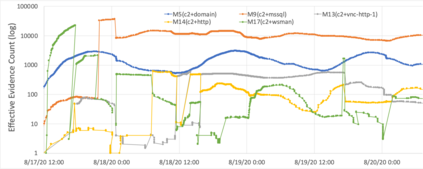
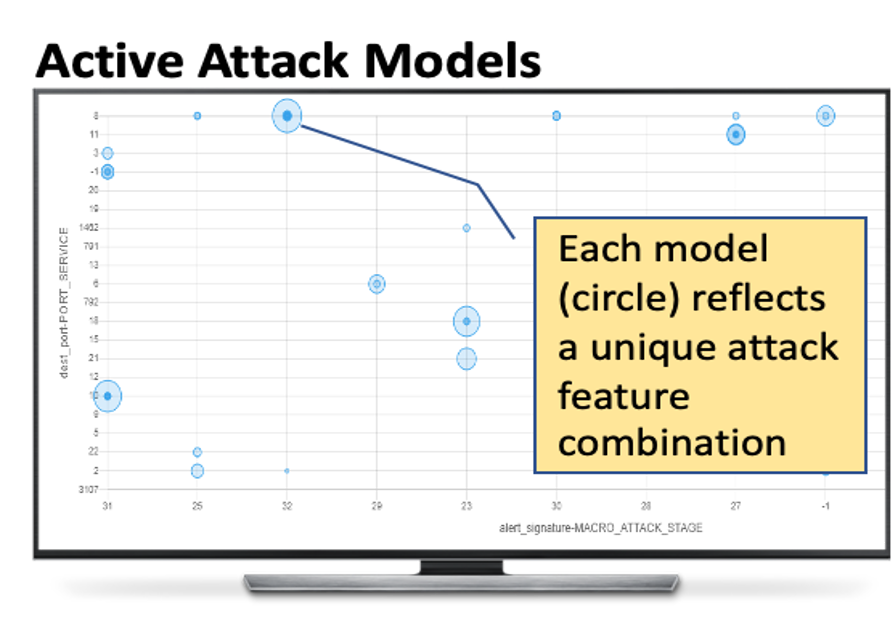
Critical and sophisticated cyberattacks often take multitudes of reconnaissance, exploitations, and obfuscation techniques to penetrate through well protected enterprise networks. The discovery and detection of attacks, though needing continuous efforts, is no longer sufficient. Security Operation Center (SOC) analysts are overwhelmed by the significant volume of intrusion alerts without being able to extract actionable intelligence. Recognizing this challenge, this paper describes the advances and findings through deploying ASSERT to process intrusion alerts from OmniSOC in collaboration with the Center for Applied Cybersecurity Research (CACR) at Indiana University. ASSERT utilizes information theoretic unsupervised learning to extract and update `attack models' in near real-time without expert knowledge. It consumes streaming intrusion alerts and generates a small number of statistical models for SOC analysts to comprehend ongoing and emerging attacks in a timely manner. This paper presents the architecture and key processes of ASSERT and discusses a few real-world attack models to highlight the use-cases that benefit SOC operations. The research team is developing a light-weight containerized ASSERT that will be shared through a public repository to help the community combat the overwhelming intrusion alerts.
翻译:关键和复杂的网络攻击往往需要大量的侦察、利用和混淆技术,才能通过受保护的企业网络渗透。发现和发现攻击,虽然需要不断作出努力,但已经不够了。安全行动中心的分析人员被大量入侵警报所淹没,无法及时获得可采取行动的情报。本文件认识到这一挑战,描述了通过部署ASSERT处理来自OmniSOC的入侵警报而取得的进展和发现。ASSERT与印地安那大学应用网络安全研究中心(CACR)合作,利用信息理论性、不受监督的学习,在没有专家知识的情况下,在近实时提取和更新“攻击模型”。它消耗入侵警报流,并生成少量统计模型,供SOC分析人员及时了解正在发生的和正在发生的攻击。本文介绍了ASSERT的结构和关键程序,并讨论了几个真实世界攻击模型,以突出SOC业务的使用情况。研究小组正在开发一个轻量的集装箱ASSERT,将通过一个公共仓库共享,帮助社区打击大规模入侵警报。