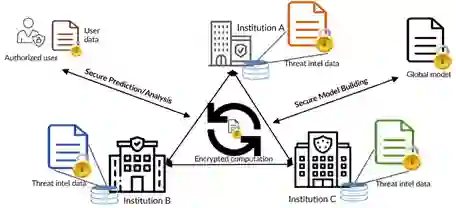
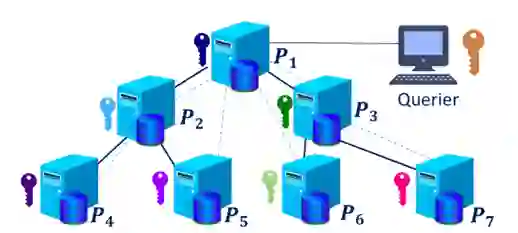
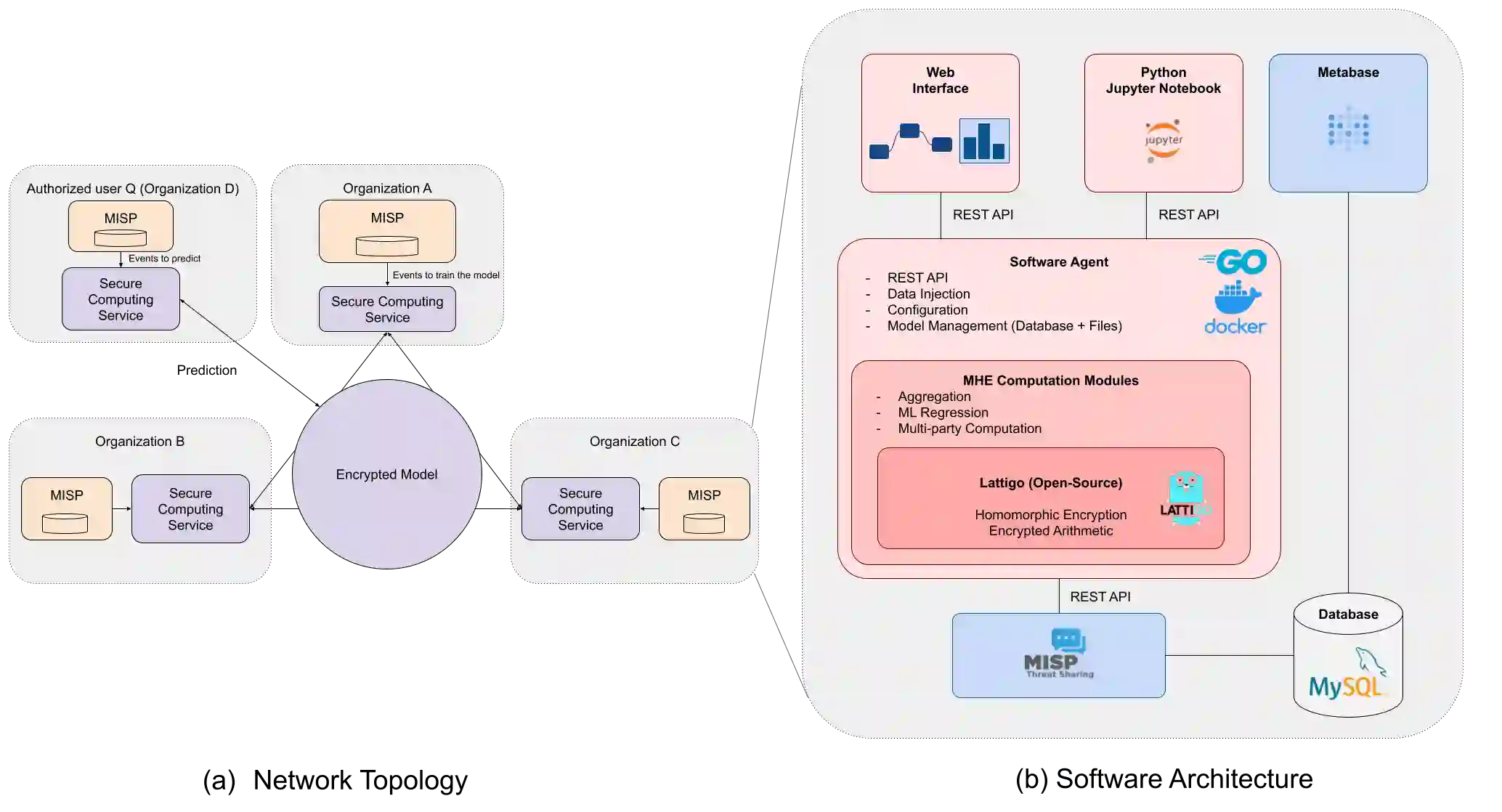
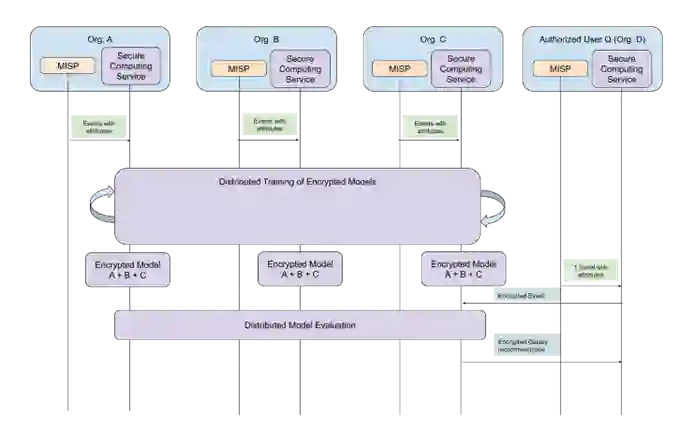
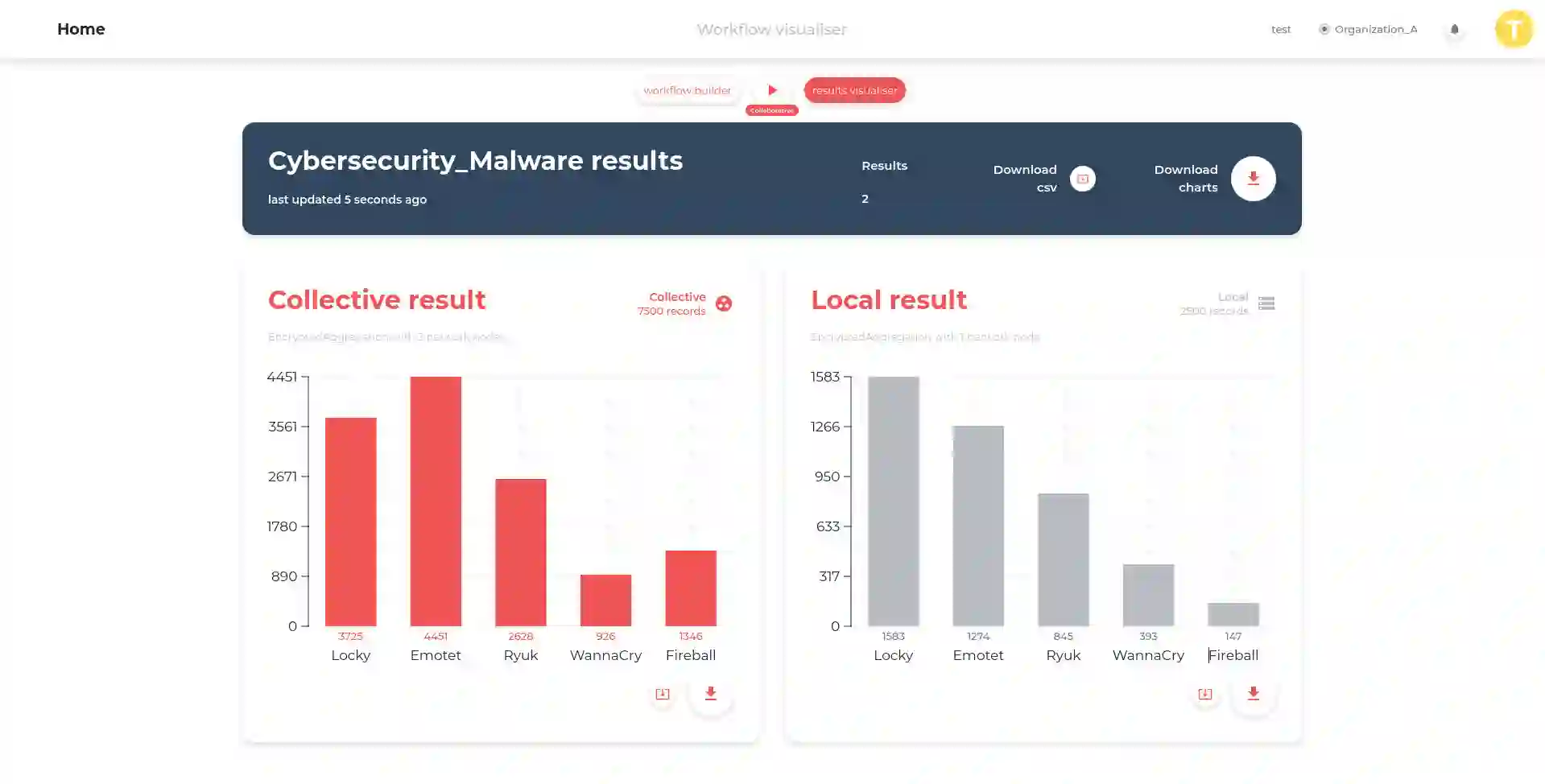
Cyber Threat Intelligence (CTI) sharing is an important activity to reduce information asymmetries between attackers and defenders. However, this activity presents challenges due to the tension between data sharing and confidentiality, that result in information retention often leading to a free-rider problem. Therefore, the information that is shared represents only the tip of the iceberg. Current literature assumes access to centralized databases containing all the information, but this is not always feasible, due to the aforementioned tension. This results in unbalanced or incomplete datasets, requiring the use of techniques to expand them; we show how these techniques lead to biased results and misleading performance expectations. We propose a novel framework for extracting CTI from distributed data on incidents, vulnerabilities and indicators of compromise, and demonstrate its use in several practical scenarios, in conjunction with the Malware Information Sharing Platforms (MISP). Policy implications for CTI sharing are presented and discussed. The proposed system relies on an efficient combination of privacy enhancing technologies and federated processing. This lets organizations stay in control of their CTI and minimize the risks of exposure or leakage, while enabling the benefits of sharing, more accurate and representative results, and more effective predictive and preventive defenses.
翻译:网络威胁情报(CTI)共享是减少攻击者和维权者之间信息不对称的重要活动,但是,由于数据共享和保密之间的紧张关系,这一活动提出了挑战,导致数据共享和保密之间的紧张关系,导致信息保留往往导致一个免费搭便车问题。因此,共享的信息只是冰山一角。目前的文献假定可以访问包含所有信息的中央数据库,但由于上述紧张局势,这并不总是可行的。这导致数据集不平衡或不完整,需要使用技术来扩大数据集;我们展示这些技术如何导致有偏向的结果和误导性的业绩预期。我们提出了一个新的框架,从所分发的关于事件、脆弱性和妥协指标的数据中提取CTI,并展示其在若干实际情况下的使用情况,同时结合Malware信息共享平台(MISP)介绍和讨论对CTI共享的政策影响。拟议的系统依赖于提高隐私技术和节制处理的高效组合。这让各组织能够控制其CTI,并最大限度地减少暴露或泄漏的风险,同时能够分享、更准确和更具代表性的结果以及更有效的预测和预防防御的好处。