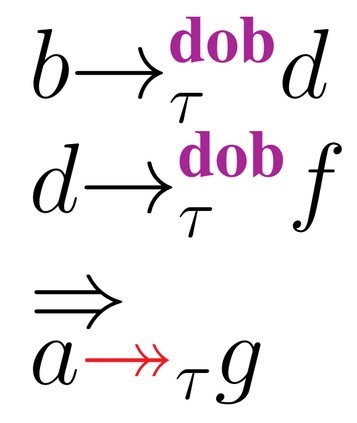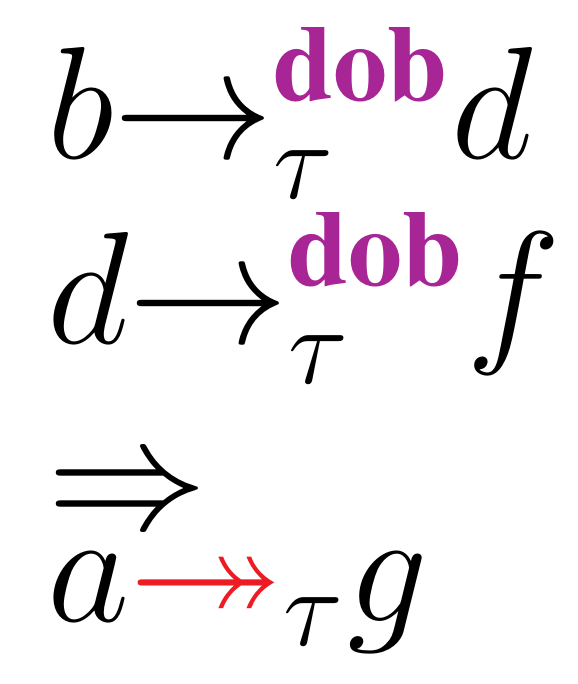We investigate the problem of runtime analysis of C11 programs under Multi-Copy-Atomic semantics (MCA). Under MCA, one can analyze program outcomes solely through interleaving and reordering of thread events. As a result, obtaining intuitive explanations of program outcomes becomes straightforward. Newer versions of ARM (ARMv8 and later), Alpha, and Intel's x-86 support MCA. Our tests reveal that state-of-the-art dynamic verification techniques that analyze program executions under the C11 memory model generate safety property violations that can be interpreted as false alarms under MCA semantics. Sorting the true from false violations puts an undesirable burden on the user. In this work, we provide a dynamic verification technique (MoCA) to analyze C11 program executions which are permitted under the MCA model. We design a happens-before relation and introduce coherence rules to capture precisely those C11 program executions which are allowed under the MCA model. MoCA's exploration of the state-space is based on the state-of-the-art dynamic verification algorithm, source-DPOR. Our experiments validate that MoCA captures all coherent C11 program executions, and is precise for the MCA model.
翻译:我们调查了在多复读-Atomic 语义学下对 C11 程序进行运行时间分析的问题。 在 MCA 下, 人们只能通过对线性事件进行中断和重新排序来分析程序结果。 因此, 获得对程序结果的直观解释变得简单明了。 ARM( ARMV8 及以后)、 Alpha 和 Intel的 X- 86 支持MCA 的新版本。 我们的测试显示, 分析C11 记忆模型下方案执行的最先进的动态核查技术会产生安全财产违规现象, 在 MCA 语义学下可以被解释为虚假警报。 从错误的违规中分选真实真相给用户带来一个不可取的负担。 在这项工作中, 我们提供了一种动态的核查技术(MCA) 分析 C11 方案执行过程,这是MCA 模式下允许的。 我们设计了一个偶然的关联,并引入了一致的规则来准确捕捉捉到那些C11 。 MACA 对州空间的探索是基于最先进的动态核查算法, 源-DPOR 。 我们的实验验证了MCA 准确的MCA 程序 。