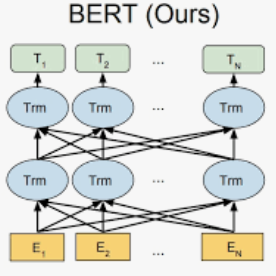
Due to the rising number of sophisticated customer functionalities, electronic control units (ECUs) are increasingly integrated into modern automotive systems. However, the high connectivity between the in-vehicle and the external networks paves the way for hackers who could exploit in-vehicle network protocols' vulnerabilities. Among these protocols, the Controller Area Network (CAN), known as the most widely used in-vehicle networking technology, lacks encryption and authentication mechanisms, making the communications delivered by distributed ECUs insecure. Inspired by the outstanding performance of bidirectional encoder representations from transformers (BERT) for improving many natural language processing tasks, we propose in this paper ``CAN-BERT", a deep learning based network intrusion detection system, to detect cyber attacks on CAN bus protocol. We show that the BERT model can learn the sequence of arbitration identifiers (IDs) in the CAN bus for anomaly detection using the ``masked language model" unsupervised training objective. The experimental results on the ``Car Hacking: Attack \& Defense Challenge 2020" dataset show that ``CAN-BERT" outperforms state-of-the-art approaches. In addition to being able to identify in-vehicle intrusions in real-time within 0.8 ms to 3 ms w.r.t CAN ID sequence length, it can also detect a wide variety of cyberattacks with an F1-score of between 0.81 and 0.99.
翻译:由于先进的客户功能越来越多,电子控制单位(ECUs)日益融入现代汽车系统,然而,由于车辆和外部网络之间的高度连通性,为能够利用车辆网络协议弱点的黑客铺平了道路。在这些协议中,主计长地区网络(CAN)是汽车联网技术中最常用的,缺乏加密和认证机制,使分布式ECUs提供的通信变得不安全。受改进许多自然语言处理任务的变压器(BERT)双向编码器(BERT)的出色表现的启发,我们在本文件中提议,“CAN-BERT”是一个深层次的基于学习的网络入侵探测系统,用来探测对CAN公共汽车协议的网络攻击。我们表明,BERT模型可以学习CAN公共汽车客车上的仲裁识别器(IDs)的序列,以便使用“大规模语言模型”不受监督的培训目标。“Car Hacking:攻击 国防挑战 2020” 的实验结果显示,“CAN-BERT”系统在0.8-BAR1号内部,还可以识别一个直径直径直径直径的服务器的频率。