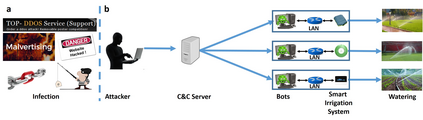
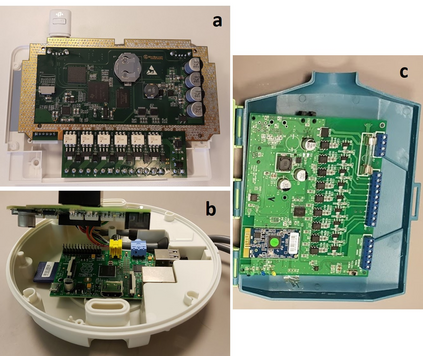
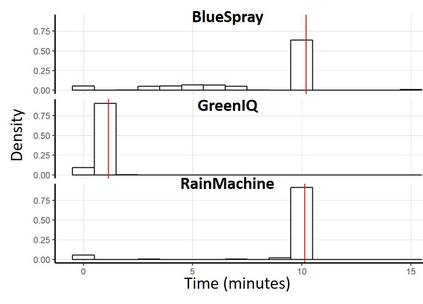
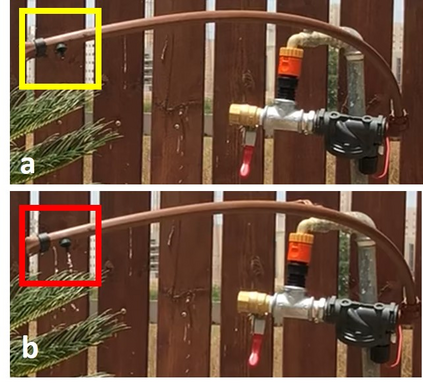
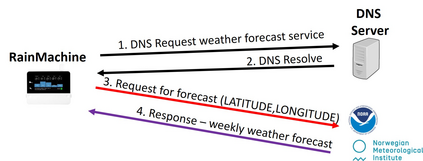
The current generation of IoT devices is being used by clients and consumers to regulate resources (such as water and electricity) obtained from critical infrastructure (such as urban water services and smart grids), creating a new attack vector against critical infrastructure. In this research we show that smart irrigation systems, a new type of green technology and IoT device aimed at saving water and money, can be used by attackers as a means of attacking urban water services. We present a distributed attack model that can be used by an attacker to attack urban water services using a botnet of commercial smart irrigation systems. Then, we show how a bot running on a compromised device in a LAN can:(1) detect a connected commercial smart irrigation system (RainMachine, BlueSpray, and GreenIQ) within 15 minutes by analyzing LAN's behavior using a dedicated classification model, and (2) launch watering via a commercial smart irrigation system according to an attacker's wishes using spoofing and replay attacks. In addition, we model the damage that can be caused by performing such an attack and show that a standard water tower can be emptied in an hour using a botnet of 1,355 sprinklers and a flood water reservoir can be emptied overnight using a botnet of 23,866 sprinklers. Finally, we discuss countermeasure methods and hypothesize whether the next generation of plumbers will use Kali Linux instead of a monkey wrench.
翻译:客户和消费者正在使用目前新一代的IOT设备来管理从关键基础设施(如城市供水服务和智能电网)获得的资源(如水电),对关键基础设施形成新的攻击矢量。在这项研究中,我们表明智能灌溉系统、新型绿色技术和IOT设备可以被攻击者用作攻击城市供水服务的手段。我们展示了一个分布式攻击模型,攻击者可以利用商业智能灌溉系统的吸管网攻击城市供水服务。然后,我们展示了在局域网的受损装置上运行的机器人如何:(1) 在15分钟内探测一个连接的商业智能灌溉系统(RainMAchine、蓝Spray和GreenIQ),方法是使用专门的分类模型分析局的行踪,以及(2) 利用攻击者的愿望,利用喷雾和重现攻击者攻击者的攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击性攻击。此外,我们模拟了这种攻击性攻击可能造成的破坏,并显示一个标准水塔可以在一小时内用一个双层的BOTnet进行清空空空清时,我们是否使用23号的蒸气瓶的蒸气瓶,最后将进行。