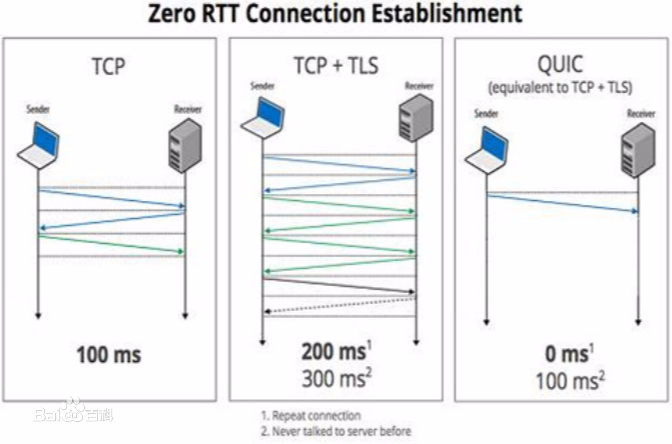
The domain name system (DNS) that maps alphabetic names to numeric Internet Protocol (IP) addresses plays a foundational role for Internet communications. By default, DNS queries and responses are exchanged in unencrypted plaintext, and hence, can be read and/or hijacked by third parties. To protect user privacy, the networking community has proposed standard encryption technologies such as DNS over TLS (DoT), DNS over HTTPS (DoH), and DNS over QUIC (DoQ) for DNS communications, enabling clients to perform secure and private domain name lookups. We survey the DNS encryption literature published since 2016, focusing on its current landscape and how it is misused by malware, and highlighting the existing techniques developed to make inferences from encrypted DNS traffic. First, we provide an overview of various standards developed in the space of DNS encryption and their adoption status, performance, benefits, and security issues. Second, we highlight ways that various malware families can exploit DNS encryption to their advantage for botnet communications and/or data exfiltration. Third, we discuss existing inference methods for profiling normal patterns and/or detecting malicious encrypted DNS traffic. Several directions are presented to motivate future research in enhancing the performance and security of DNS encryption.
翻译:用于绘制数字互联网协议地址的字母名称的域名系统(DNS)在互联网通信中起着基础作用,默认情况下,DNS查询和答复以未加密的普通文本交换,因此可以被第三方读取和/或劫持。为了保护用户隐私,网络社区提出了标准加密技术,如DNS在TLS(DoT)上、DNS在HTTPS(DH)上、DNS在QUIC(QQ)上为DNS通信进行加密,使客户能够进行安全和私人域名查询。我们调查自2016年以来出版的DNS加密文献,重点是其当前景观和恶意软件如何滥用,并突出从加密DNS交通中作出推断的现有技术。首先,我们概述了在DNS加密空间开发的各种标准及其采用状态、性能、效益和安全问题。第二,我们强调各种恶意家庭利用DNS加密来获取对电脑网络通信和/或数据过滤的好处。第三,我们讨论了目前用于加强正常通信性能和对安全性能进行加密的可靠加密方法。