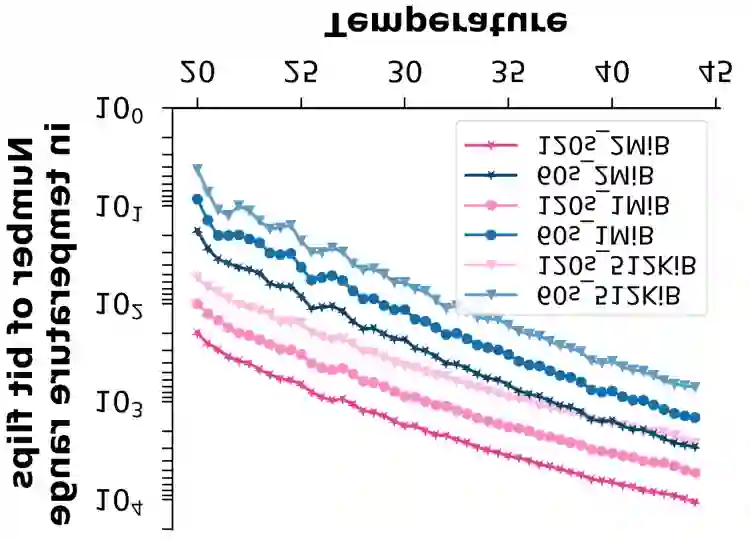
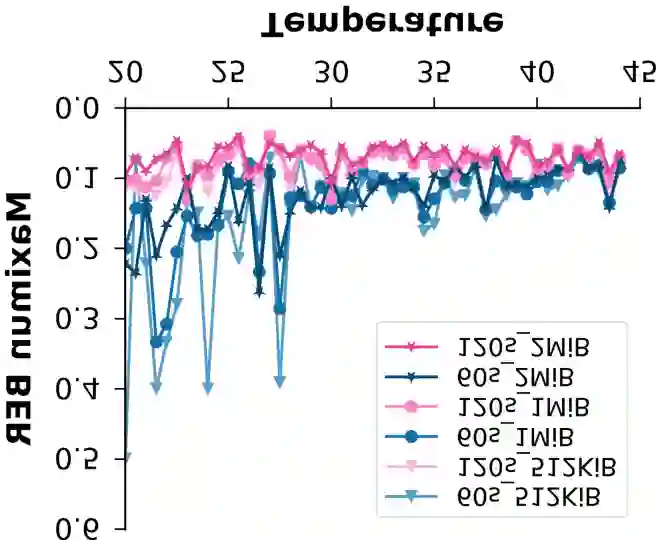
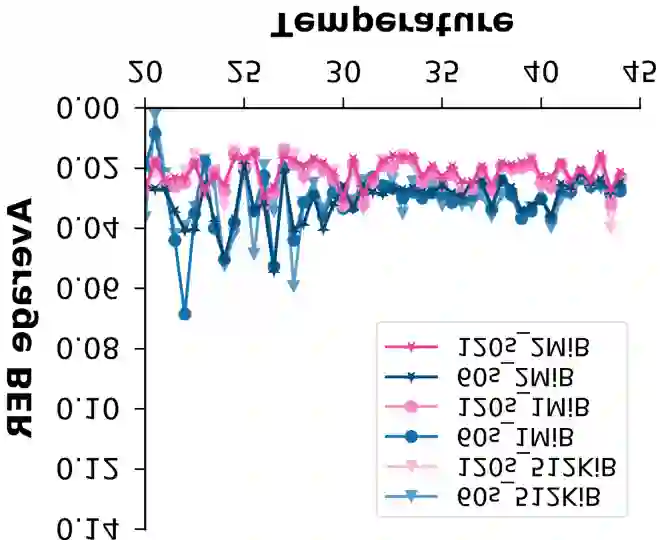
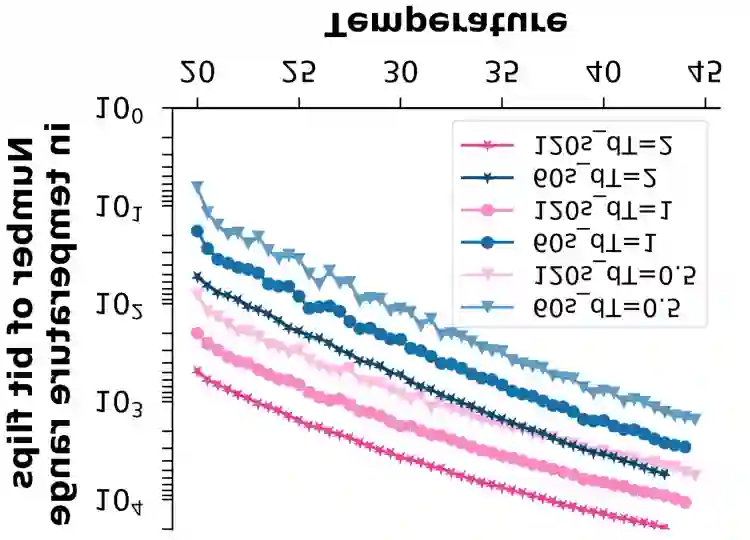
The ubiquity and pervasiveness of modern Internet of Things (IoT) devices opens up vast possibilities for novel applications, but simultaneously also allows spying on, and collecting data from, unsuspecting users to a previously unseen extent. This paper details a new attack form in this vein, in which the decay properties of widespread, off-the-shelf DRAM modules are exploited to accurately sense the temperature in the vicinity of the DRAM-carrying device. Among others, this enables adversaries to remotely and purely digitally spy on personal behavior in users' private homes, or to collect security-critical data in server farms, cloud storage centers, or commercial production lines. We demonstrate that our attack can be performed by merely compromising the software of an IoT device and does not require hardware modifications or physical access at attack time. It can achieve temperature resolutions of up to 0.5{\deg}C over a range of 0{\deg}C to 70{\deg}C in practice. Perhaps most interestingly, it even works in devices that do not have a dedicated temperature sensor on board. To complete our work, we discuss practical attack scenarios as well as possible countermeasures against our temperature espionage attacks.
翻译:现代事物互联网(IOT)装置的无处不在和普及,为新应用提供了巨大的可能性,但同时也允许在先前的不为人知的范围内监视和收集来自不为人知的用户的数据。本文详细介绍了这种脉冲中的一种新的攻击形式,即广泛、现成的DRAM模块的衰变特性被利用来准确感应DRAM携带装置附近的温度。除其他外,这使对手能够对用户私人家中的个人行为进行远程和纯数字的间谍,或收集服务器、云存储中心或商业生产线的安全关键数据。我们证明,我们的攻击可以仅仅通过破坏IOT装置的软件来进行,而不需要在攻击时间进行硬件改造或实际进入。它可以在实际操作中达到0.5的温度分辨率,范围在0到70米德克之间。也许最有意思的是,它甚至在机上没有专门的温度传感器的装置中起作用。为了完成我们的工作,我们讨论实际的攻击情景,作为防止温度攻击的可能反措施。