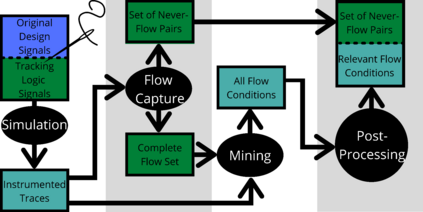
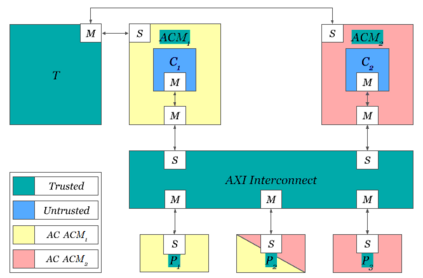
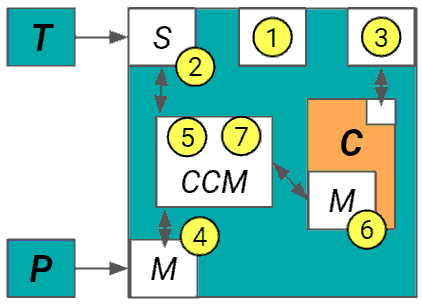
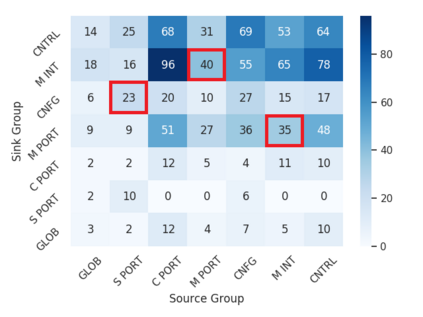
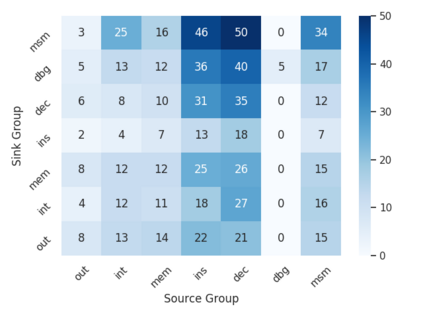
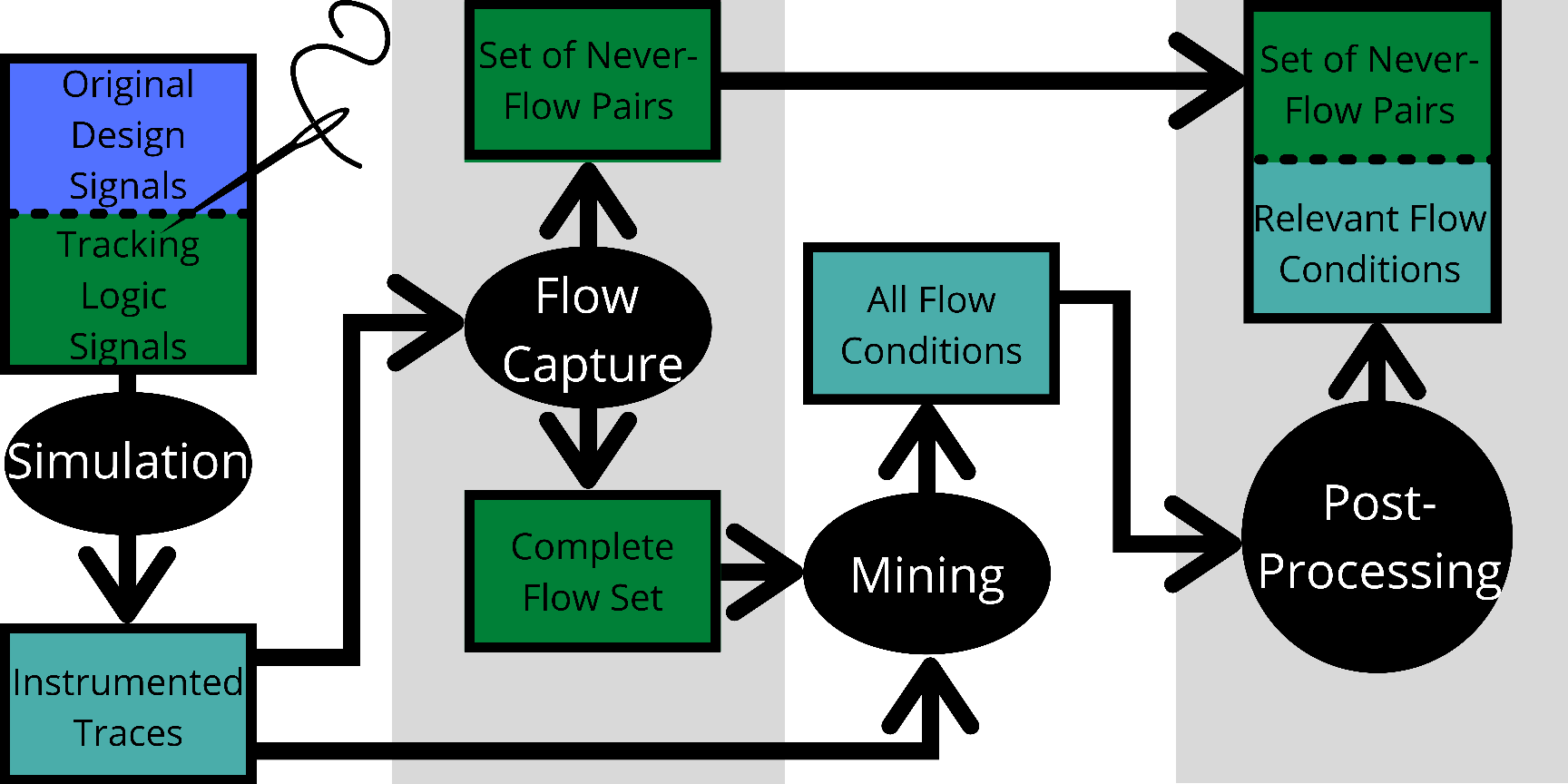
We present a methodology for creating information flow specifications of hardware designs. Such specifications can help designers better understand their design and are necessary for security validation processes. By combining information flow tracking and specification mining, we are able to produce information flow properties of a design without prior knowledge of security agreements or specifications. We develop a tool, Isadora, to evaluate our methodology. We demonstrate Isadora may define the information flows within an access control module in isolation and within an SoC and over a RISC-V design. Over the access control module, Isadora mined output completely covers an assertion based security specification of the design provided by the designers. For both the access control module and RISC-V, we sample Isadora output properties and find 10 out of 10 and 8 out of 10 properties, respectively, define the design behavior to relevant to a Common Weakness Enumeration (CWE). We find our methodology may independently mine security properties manually developed by hardware designers, automatically generate properties describing CWEs over a design, and scale to SoC and CPU designs.
翻译:我们提出了设计硬件设计的信息流规格的方法。这种规格可以帮助设计者更好地了解其设计,并且是安全验证过程所必需的。通过将信息流跟踪和规格采矿结合起来,我们能够产生一个设计中的信息流特性,而没有事先了解安全协议或规格;我们开发了一个工具Isadora来评估我们的方法。我们证明Isadora可以孤立地、在一个SoC内部和在RISC-V设计上界定一个出入控制模块内的信息流动。在出入控制模块中,Isadora 开采的产出完全包含设计者提供的设计基于安全规格的断言性规格。对于访问控制模块和RISC-V,我们抽样测试Isadora输出特性,在10个特性中分别发现10个和8个特性中的10个特性,界定了与共同弱点计算相关的设计行为。我们发现我们的方法可以独立地界定硬件设计者人工开发的地雷安全特性,自动产生设计中描述CWE的特性,以及规模到SoC和CPU设计的特性。