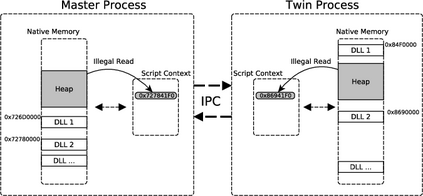
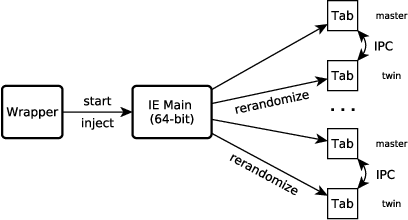
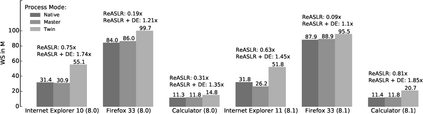
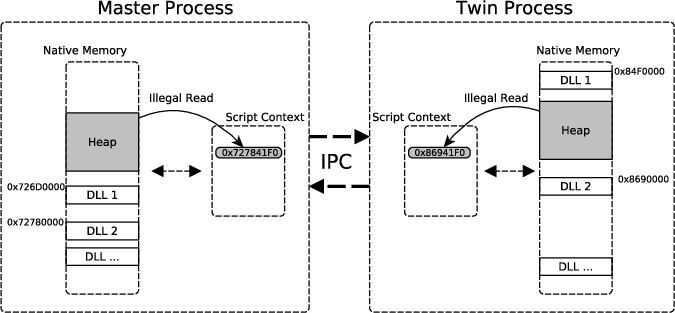
Memory disclosure attacks play an important role in the exploitation of memory corruption vulnerabilities. By analyzing recent research, we observe that bypasses of defensive solutions that enforce control-flow integrity or attempt to detect return-oriented programming require memory disclosure attacks as a fundamental first step. However, research lags behind in detecting such information leaks. In this paper, we tackle this problem and present a system for fine-grained, automated detection of memory disclosure attacks against scripting engines. The basic insight is as follows: scripting languages, such as JavaScript in web browsers, are strictly sandboxed. They must not provide any insights about the memory layout in their contexts. In fact, any such information potentially represents an ongoing memory disclosure attack. Hence, to detect information leaks, our system creates a clone of the scripting engine process with a re-randomized memory layout. The clone is instrumented to be synchronized with the original process. Any inconsistency in the script contexts of both processes appears when a memory disclosure was conducted to leak information about the memory layout. Based on this detection approach, we have designed and implemented Detile (\underline{det}ection of \underline{i}nformation \underline{le}aks), a prototype for the JavaScript engine in Microsoft's Internet Explorer 10/11 on Windows 8.0/8.1. An empirical evaluation shows that our tool can successfully detect memory disclosure attacks even against this proprietary software.
翻译:内存披露攻击在利用记忆腐败脆弱性方面起着重要作用。 通过分析最近的研究, 我们观察到, 绕过执行控制流完整性或试图检测返回导向程序制作的防御性解决方案, 需要作为基本的第一步进行记忆披露攻击。 但是, 研究在发现这类信息泄漏方面落后于最初阶段。 在本文中, 我们解决这个问题, 并展示一个微小的、 自动检测对脚本引擎的记忆披露攻击的系统。 基本见解如下: 文字语言, 如网络浏览器中的 JavaScript 等, 被严格置于沙箱中。 它们不能提供关于其背景下的内存布局的任何洞见。 事实上, 任何这类信息都有可能是持续记忆披露攻击。 因此, 要检测信息泄漏, 我们的系统会创建一个编程引擎进程的克隆, 并重新调整记忆布局。 当进行记忆披露时, 两个过程的脚本背景中的任何不一致之处都会出现。 基于这一探测方法, 我们设计并实施了Detile( 甚至是直线 { dedetratline) a developmental developmental developtraction) a 10reval demagistrations demagistration 。