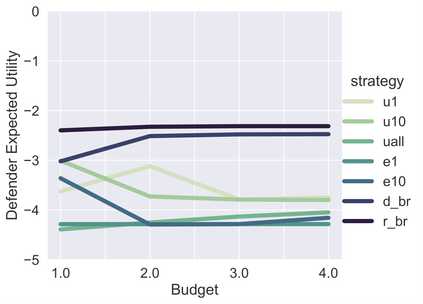
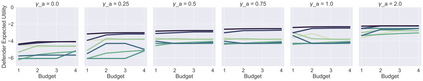
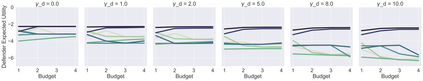
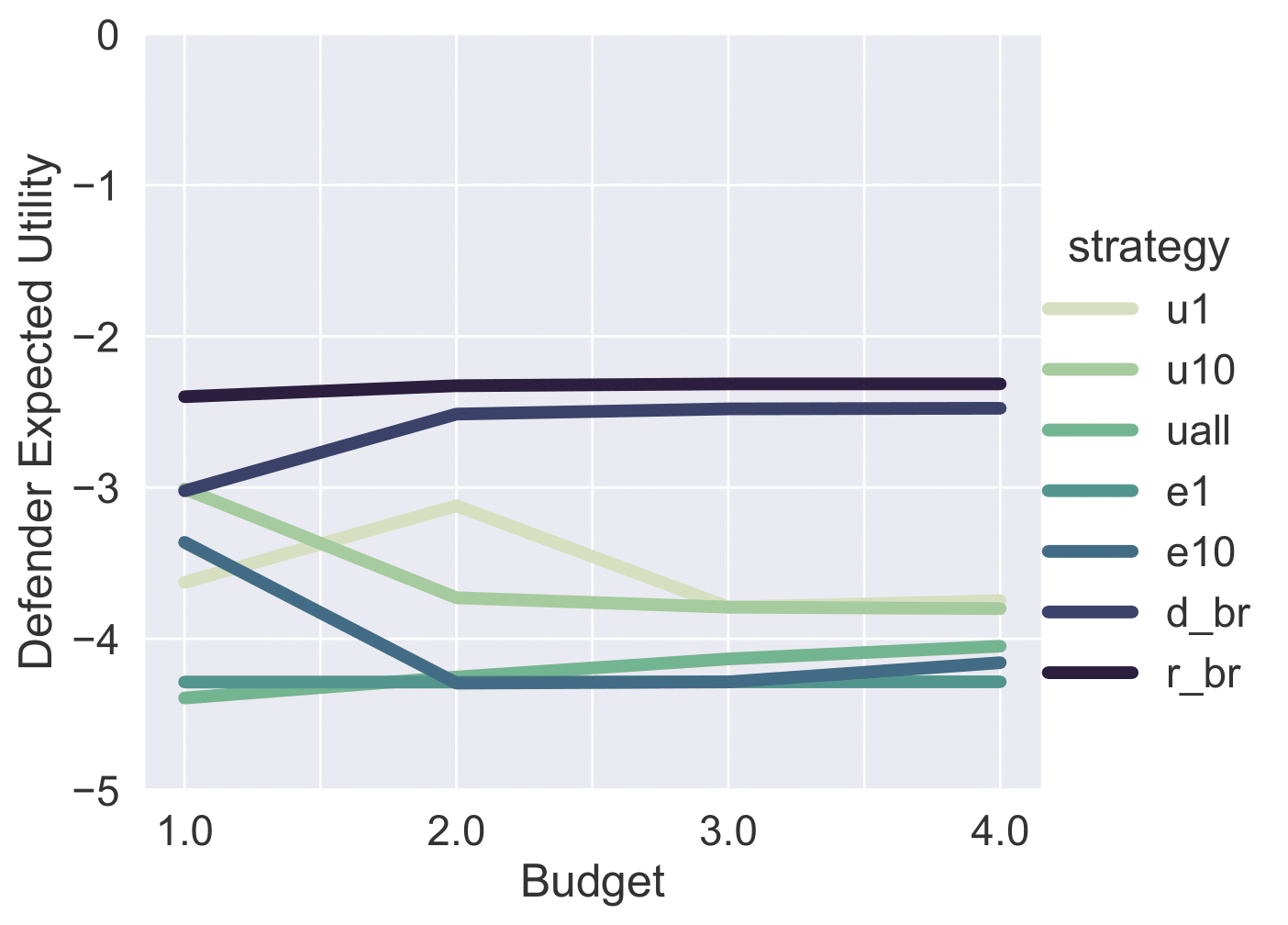
Malware attacks are costly. To mitigate against such attacks, organizations deploy malware detection tools that help them detect and eventually resolve those threats. While running only the best available tool does not provide enough coverage of the potential attacks, running all available tools is prohibitively expensive in terms of financial cost and computing resources. Therefore, an organization typically runs a set of tools that maximizes their coverage given a limited budget. However, how should an organization choose that set? Attackers are strategic, and will change their behavior to preferentially exploit the gaps left by a deterministic choice of tools. To avoid leaving such easily-exploited gaps, the defender must choose a random set. In this paper, we present an approach to compute an optimal randomization over size-bounded sets of available security analysis tools by modeling the relationship between attackers and security analysts as a leader-follower Stackelberg security game. We estimate the parameters of our model by combining the information from the VirusTotal dataset with the more detailed reports from the National Vulnerability Database. In an empirical comparison, our approach outperforms a set of natural baselines under a wide range of assumptions.
翻译:恶意攻击是昂贵的。 为了减轻这种攻击,组织会部署恶意软件检测工具,帮助他们发现并最终消除这些威胁。虽然仅使用现有最佳工具不足以覆盖潜在攻击,但运行所有可用工具在财务成本和计算资源方面费用极其昂贵。因此,一个组织通常使用一套工具,在预算有限的情况下最大限度地扩大其覆盖面。然而,一个组织应如何选择这套工具?攻击者是战略性的,并将改变其行为,优先利用确定性选择工具留下的差距。为了避免留下这种容易利用的漏洞,辩护人必须选择一套随机工具。在本文件中,我们提出一种方法,通过模拟攻击者和安全分析师作为领导人-追随者斯塔克尔伯格安全游戏的关系,对攻击者与安全分析师之间的关系进行最佳随机化计算,我们通过将病毒Totar数据集中的信息与国家脆弱性数据库的更详细报告结合起来来估计我们的模型参数。在经验比较中,我们的方法比一系列假设的自然基线要强。