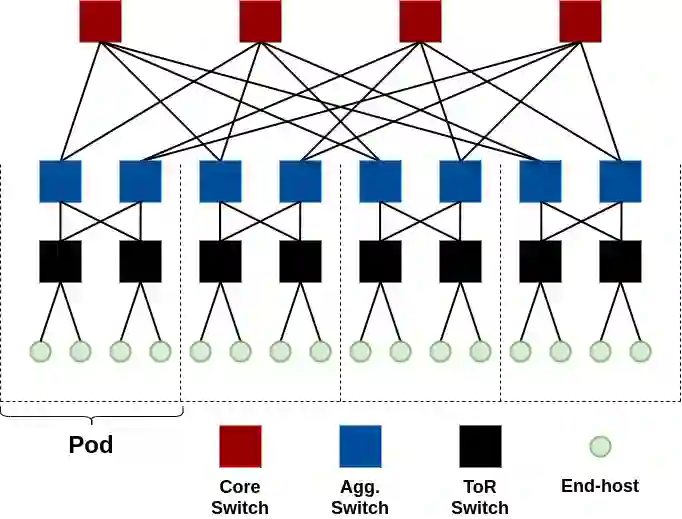
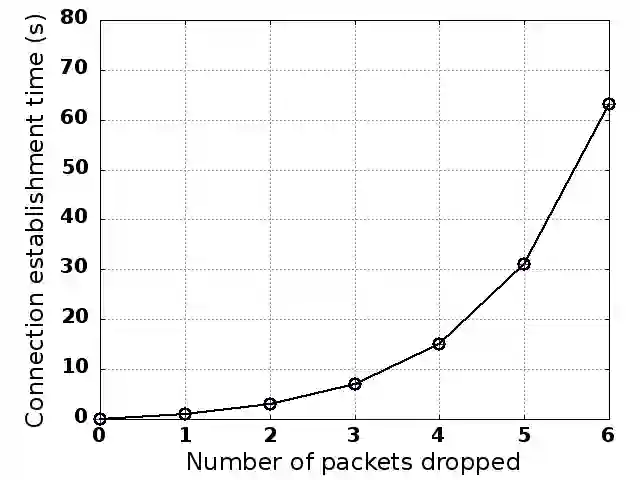
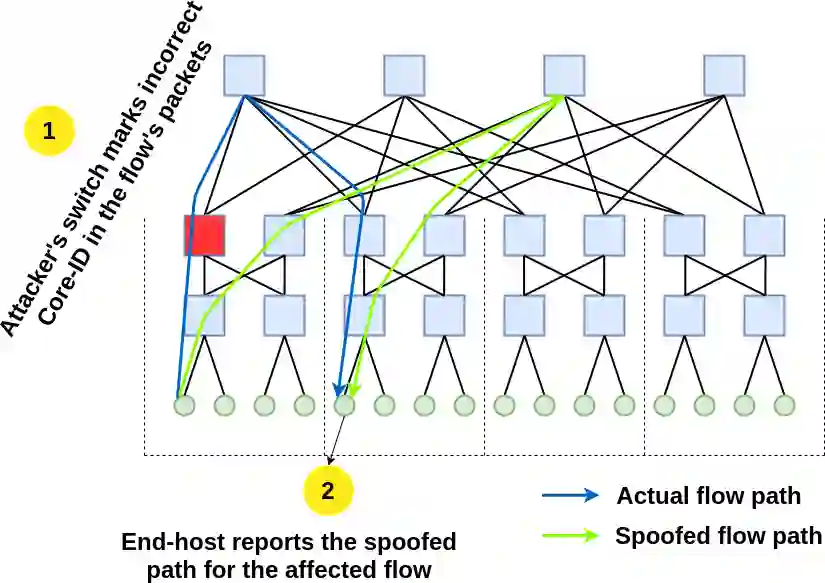
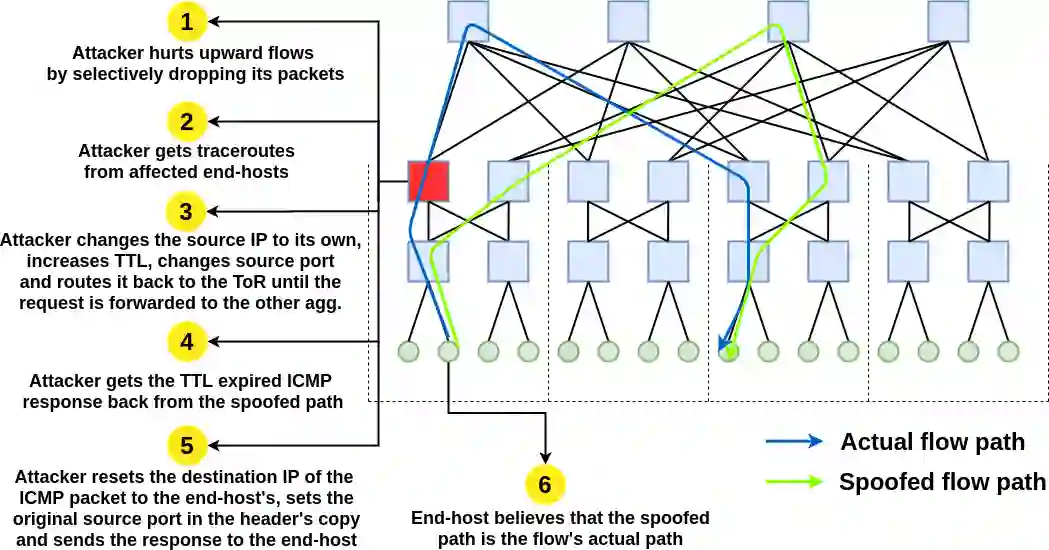
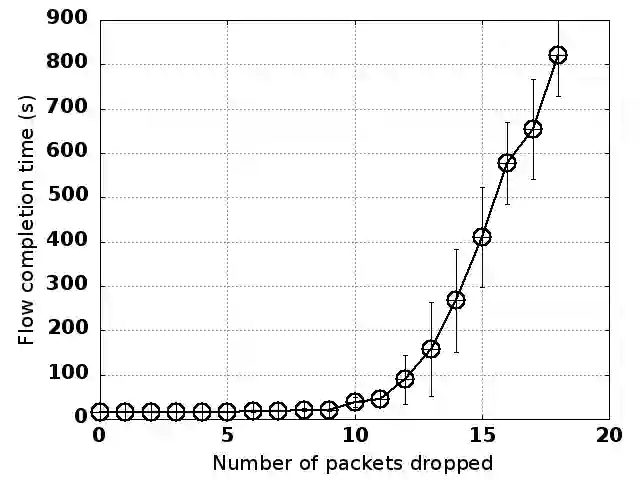
Substantial efforts are invested in improving network security, but the threat landscape is rapidly evolving, particularly with the recent interest in programmable network hardware. We explore a new security threat, from an attacker who has gained control of such devices. While it should be obvious that such attackers can trivially cause substantial damage, the challenge and novelty are in doing so while preventing quick diagnosis by the operator. We find that compromised programmable devices can easily degrade networked applications by orders of magnitude, while evading diagnosis by even the most sophisticated network diagnosis methods in deployment. Two key observations yield this result: (a) targeting a small number of packets is often enough to cause disproportionate performance degradation; and (b) new programmable hardware is an effective enabler of careful, selective targeting of packets. Our results also point to recommendations for minimizing the damage from such attacks, ranging from known, easy to implement techniques like encryption and redundant requests, to more complex considerations that would potentially limit some intended uses of programmable hardware. For data center contexts, we also discuss application-aware monitoring and response as a potential mitigation.
翻译:在改善网络安全方面投入了大量努力,但威胁环境正在迅速演变,特别是最近对可编程网络硬件的兴趣正在迅速演变。我们探索了一个新的安全威胁,来自已经控制了这些装置的攻击者。虽然这种攻击者显然可以轻描淡写地造成重大破坏,但挑战与新颖之处在于这样做,同时防止操作者的快速诊断。我们发现,失密的可编程装置可以很容易地按数量级降低网络应用程序的功能,同时甚至以最尖端的网络诊断方法在部署时回避诊断。有两点关键观测得出这一结果:(a) 瞄准少量的包往往足以造成不相称的性能退化;(b) 新的可编程硬件是谨慎、有选择地瞄准包件的有效工具。我们的结果还表明,如何尽量减少这类攻击造成的损害,从已知的、易于执行加密和冗余请求等技术,到可能限制可编程硬件某些预期用途的更为复杂的考虑因素,我们还要讨论应用的监测和反应,作为可能的缓解措施。