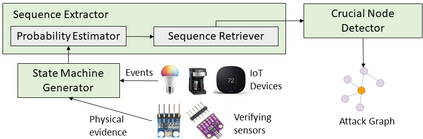
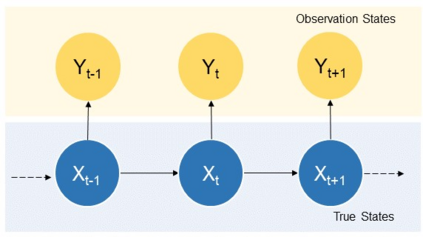
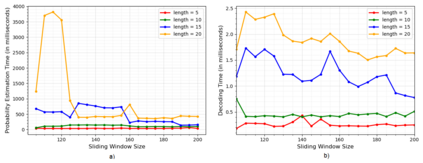
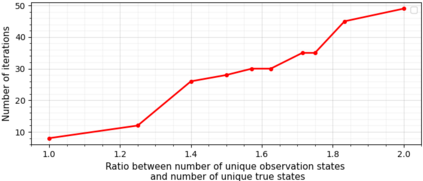
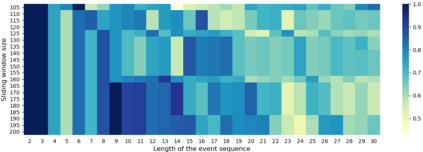
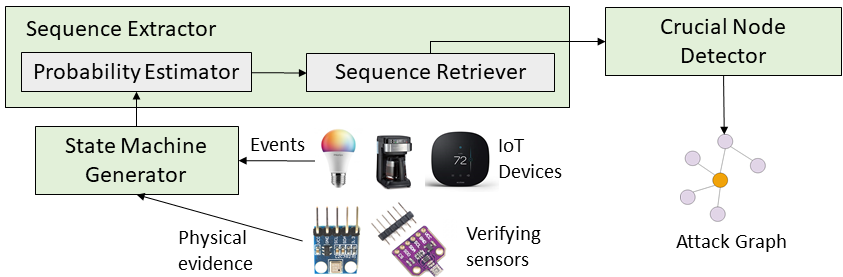
With the emergence and fast development of trigger-action platforms in IoT settings, security vulnerabilities caused by the interactions among IoT devices become more prevalent. The event occurrence at one device triggers an action in another device, which may eventually contribute to the creation of a chain of events in a network. Adversaries exploit the chain effect to compromise IoT devices and trigger actions of interest remotely just by injecting malicious events into the chain. To address security vulnerabilities caused by trigger-action scenarios, existing research efforts focus on the validation of the security properties of devices or verification of the occurrence of certain events based on their physical fingerprints on a device. We propose IoTMonitor, a security analysis system that discerns the underlying chain of event occurrences with the highest probability by observing a chain of physical evidence collected by sensors. We use the Baum-Welch algorithm to estimate transition and emission probabilities and the Viterbi algorithm to discern the event sequence. We can then identify the crucial nodes in the trigger-action sequence whose compromise allows attackers to reach their final goals. The experiment results of our designed system upon the PEEVES datasets show that we can rebuild the event occurrence sequence with high accuracy from the observations and identify the crucial nodes on the attack paths.
翻译:随着在IoT环境中触发行动平台的出现和快速发展,由IoT装置相互作用造成的安全脆弱性更加普遍。在一个装置上发生的事件触发了另一个装置的动作,这最终可能有助于在网络中产生一系列事件。相反,利用连锁效应来破坏IoT装置,并仅仅通过向链中注入恶意事件来触发人们感兴趣的行动。为了解决触发行动情景造成的安全脆弱性,现有的研究工作侧重于验证装置的安全特性,或根据装置上的物理指纹核查某些事件的发生情况。我们建议使用IoTMonitor,一个安全分析系统,通过观察传感器收集的一系列实物证据,以最大的概率辨别事件发生的潜在链。我们使用 Baum-Welch 算法来估计转移和排放概率,以及Vitebi 算法来辨别事件序列。然后我们可以确定触发行动序列中的关键节点,这些节点的妥协使攻击者能够达到最终目标。我们在PEEVES数据集中设计的系统实验结果显示,我们能够从攻击的观察中重建事件的高度序列。