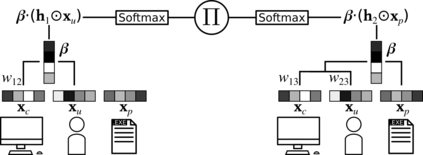
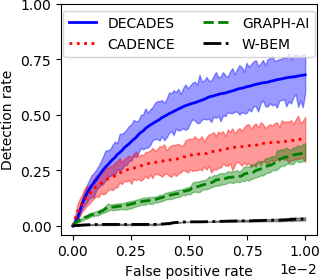
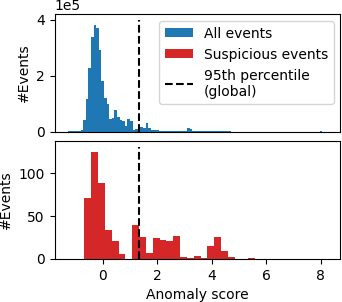
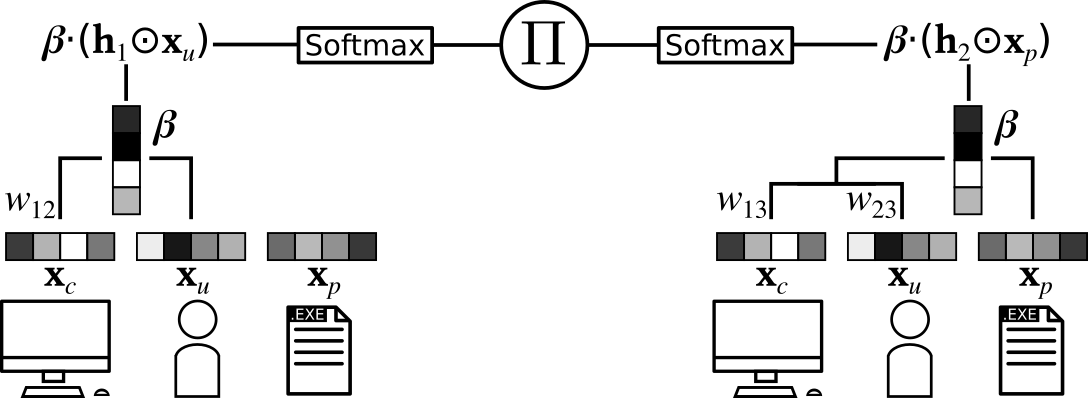
Anomaly detection in event logs is a promising approach for intrusion detection in enterprise networks. By building a statistical model of usual activity, it aims to detect multiple kinds of malicious behavior, including stealthy tactics, techniques and procedures (TTPs) designed to evade signature-based detection systems. However, finding suitable anomaly detection methods for event logs remains an important challenge. This results from the very complex, multi-faceted nature of the data: event logs are not only combinatorial, but also temporal and heterogeneous data, thus they fit poorly in most theoretical frameworks for anomaly detection. Most previous research focuses on either one of these three aspects, building a simplified representation of the data that can be fed to standard anomaly detection algorithms. In contrast, we propose to simultaneously address all three of these characteristics through a specifically tailored statistical model. We introduce \textsc{Decades}, a \underline{d}ynamic, h\underline{e}terogeneous and \underline{c}ombinatorial model for \underline{a}nomaly \underline{d}etection in \underline{e}vent \underline{s}treams, and we demonstrate its effectiveness at detecting malicious behavior through experiments on a real dataset containing labelled red team activity. In particular, we empirically highlight the importance of handling the multiple characteristics of the data by comparing our model with state-of-the-art baselines relying on various data representations.
翻译:事件日志中的异常探测是企业网络入侵探测的一个很有希望的方法。 通过建立通常活动的统计模型, 它的目的是检测多种恶意行为, 包括隐形战术、 技术和程序(TTPs), 旨在逃避基于签名的检测系统。 然而, 找到事件日志中适当的异常探测方法仍是一项重大挑战。 这是数据非常复杂、 多方面性质的结果: 事件日志不仅是组合式的, 而且是时间性和混杂性的数据, 因此它们在大多数异常检测的理论框架中是差的。 以往的研究大多侧重于这三个方面的任何一个方面, 建立可以提供给标准异常检测算法(TTPs) 的简化数据表达方式。 相反, 我们提议通过一个专门定制的统计模型同时处理所有三种特征。 我们引入了一种非常复杂且多面的药物、 hunderline 和\ roundline 和 munderline 各种测量模型 { crobinalatalmod 模型, 通过我们正在检测的特定数据分析的模型 显示我们系统 的多重数据记录 。