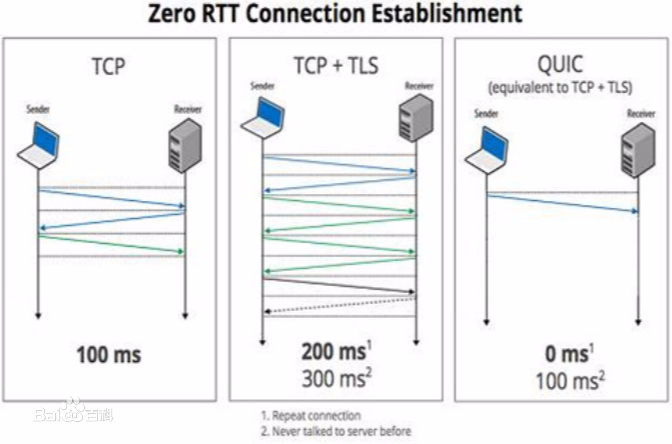
Cryptographic protocols have been widely used to protect the user's privacy and avoid exposing private information. QUIC (Quick UDP Internet Connections), as an alternative to traditional HTTP, demonstrates its unique transmission characteristics: based on UDP for encrypted resource transmission, accelerating web page rendering. However, existing encrypted transmission schemes based on TCP are vulnerable to website fingerprinting (WFP) attacks, allowing adversaries to infer the users' visited websites by eavesdropping on the transmission channel. Whether QUIC protocol can effectively resisting to such attacks is worth investigating. In this work, we demonstrated the extreme vulnerability of QUIC under WFP attacks by comparing attack results under well-designed conditions. We also study the transferability of features, which enable the adversary to use proven effective features on a special protocol attacking a new protocol. This study shows that QUIC is more vulnerable to WFP attacks than HTTPS in the early traffic scenario but is similar in the normal scenario. The maximum attack accuracy on QUIC is 56.8 % and 73 % higher than on HTTPS utilizing Simple features and Transfer features. The insecurity characteristic of QUIC explains the dramatic gap. We also find that features are transferable between protocols, and the feature importance is partially inherited on normal traffic due to the relatively fixed browser rendering sequence and the similar request-response model of protocols. However, the transferability is inefficient when on early traffic, as QUIC and HTTPS show significantly different vulnerability when considering early traffic. We also show that attack accuracy on QUIC could reach 95.4 % with only 40 packets and just using simple features, whereas only 60.7 % when on HTTPS.
翻译:QUIC(Quick UDP Internet Connects)作为传统HTTP的替代方案,展示了它独特的传输特性:基于UDP加密资源传输的加密资源传输,加快网页制作。然而,基于TCP(WFP)的现有加密传输计划很容易受到网站指纹攻击(WFP)的伤害,允许对手通过偷听传输频道窃听用户访问的网站,推断用户访问的网站,值得调查QUIC协议能否有效抵抗这种攻击的脆弱性。在这项工作中,我们通过在设计完善的条件下比较攻击的准确性,展示了在WFPC袭击的加密协议中使用经证明的有效功能的可传输性。然而,QUIC在早期交通情况中比HTPS更容易受到攻击,但是在正常情况下,QUIC的最大攻击准确度是56.8%和73 %。在使用简单的简单特征和传输功能时,我们发现HTPS的快速攻击能力非常脆弱。