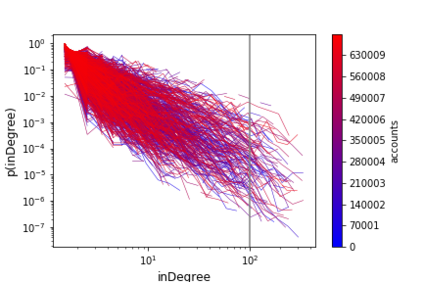
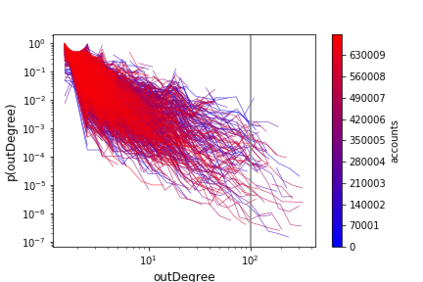
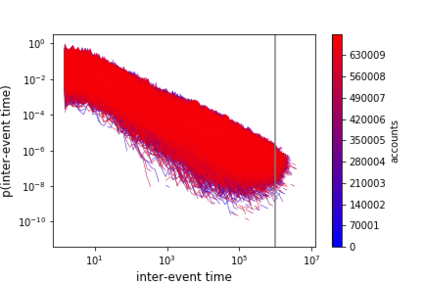
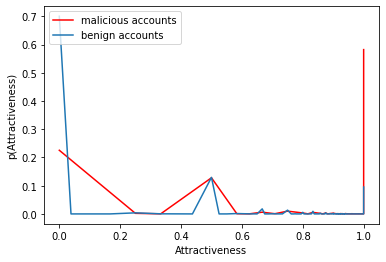
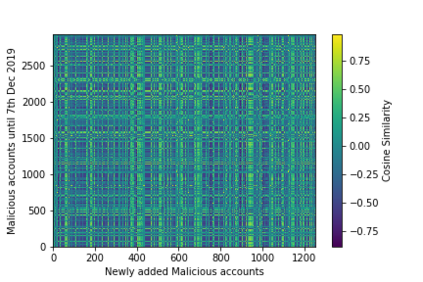
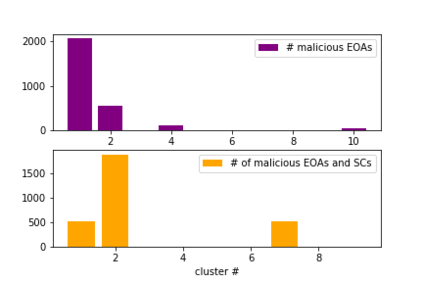
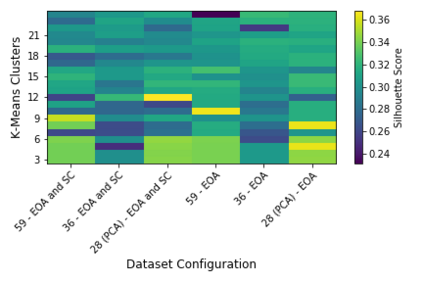
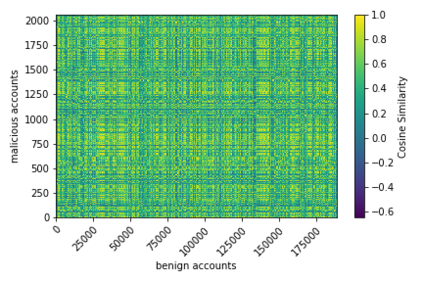
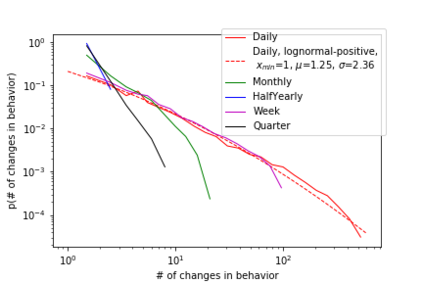
The temporal nature of modeling accounts as nodes and transactions as directed edges in a directed graph -- for a blockchain, enables us to understand the behavior (malicious or benign) of the accounts. Predictive classification of accounts as malicious or benign could help users of the permissionless blockchain platforms to operate in a secure manner. Motivated by this, we introduce temporal features such as burst and attractiveness on top of several already used graph properties such as the node degree and clustering coefficient. Using identified features, we train various Machine Learning (ML) algorithms and identify the algorithm that performs the best in detecting which accounts are malicious. We then study the behavior of the accounts over different temporal granularities of the dataset before assigning them malicious tags. For Ethereum blockchain, we identify that for the entire dataset - the ExtraTreesClassifier performs the best among supervised ML algorithms. On the other hand, using cosine similarity on top of the results provided by unsupervised ML algorithms such as K-Means on the entire dataset, we were able to detect 554 more suspicious accounts. Further, using behavior change analysis for accounts, we identify 814 unique suspicious accounts across different temporal granularities.
翻译:模拟账户作为节点和交易作为定向图表中直接边缘的标点和交易的时间性质 -- -- 对于一个链条来说,它使我们能够理解账户的行为(恶意或良性) 。 预测性地将账户分类为恶意或良性,可以帮助无许可证的块链平台的用户以安全的方式运作。 受此驱动, 我们引入了时间特征, 比如在节点度和组合系数等一些已经使用的图形属性之上, 比如爆裂和吸引力。 使用已确认的特征, 我们培训了各种机器学习算法, 并确定了在发现哪些账户是恶意账户方面表现最佳的算法。 然后, 在分配恶意标签之前,我们研究了数据集中不同时间颗粒的账户行为。 对于 Etheenum 块链, 我们发现整个数据集 - ExtraTreesClassorizer 在受监管的 ML 算法中表现最佳。 另一方面, 我们利用未经监控的 ML 运算法( 如 K- Means ) 所提供的结果之上的cos 类似性, 我们得以检测到554 更可疑的账户 。 。 此外, 我们通过对各种可疑账户进行时间性分析。