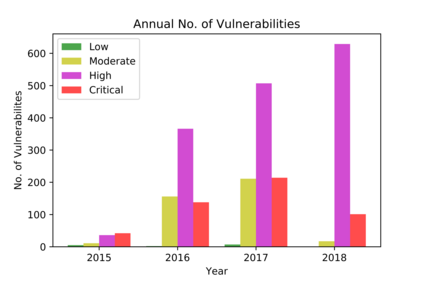
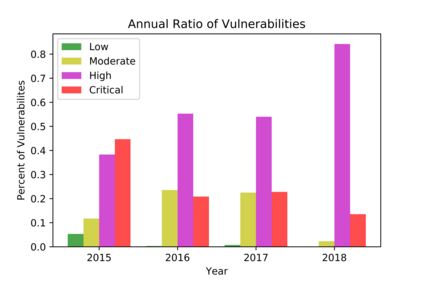
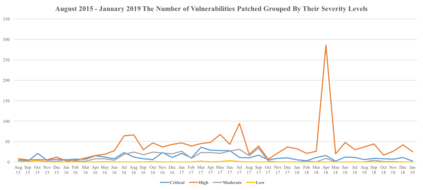
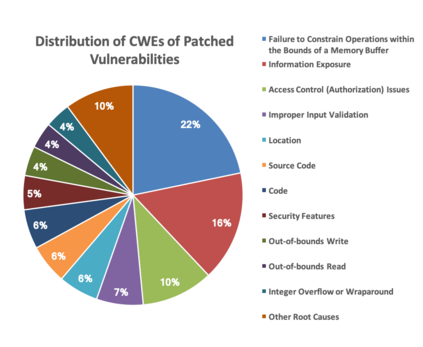
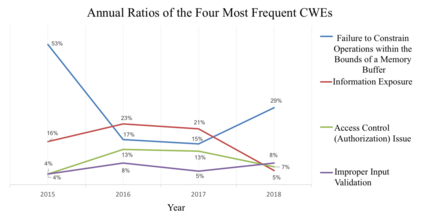
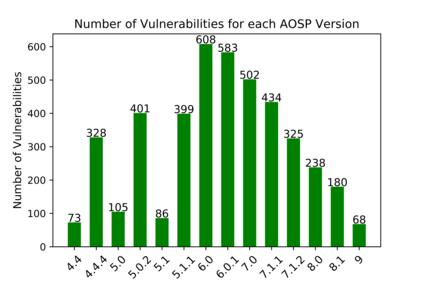
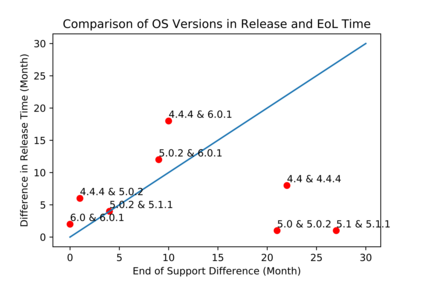
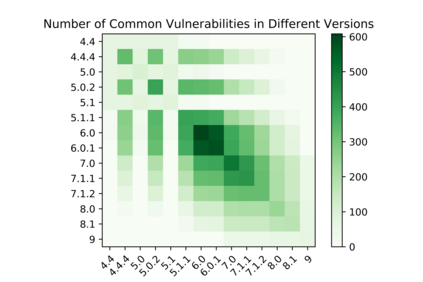
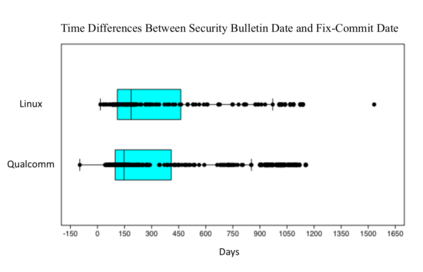
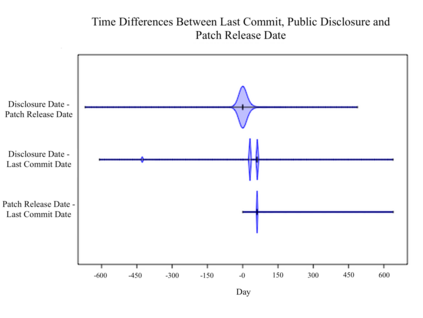
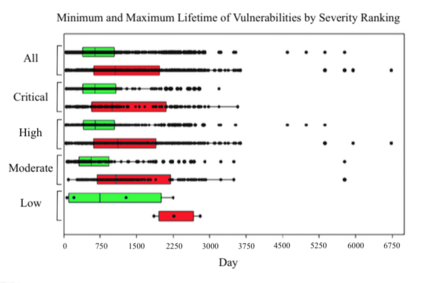
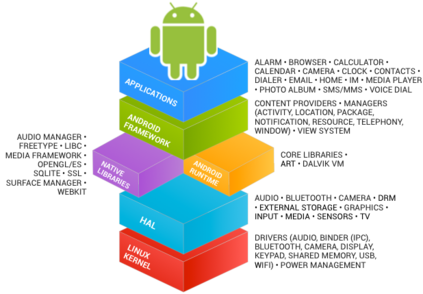
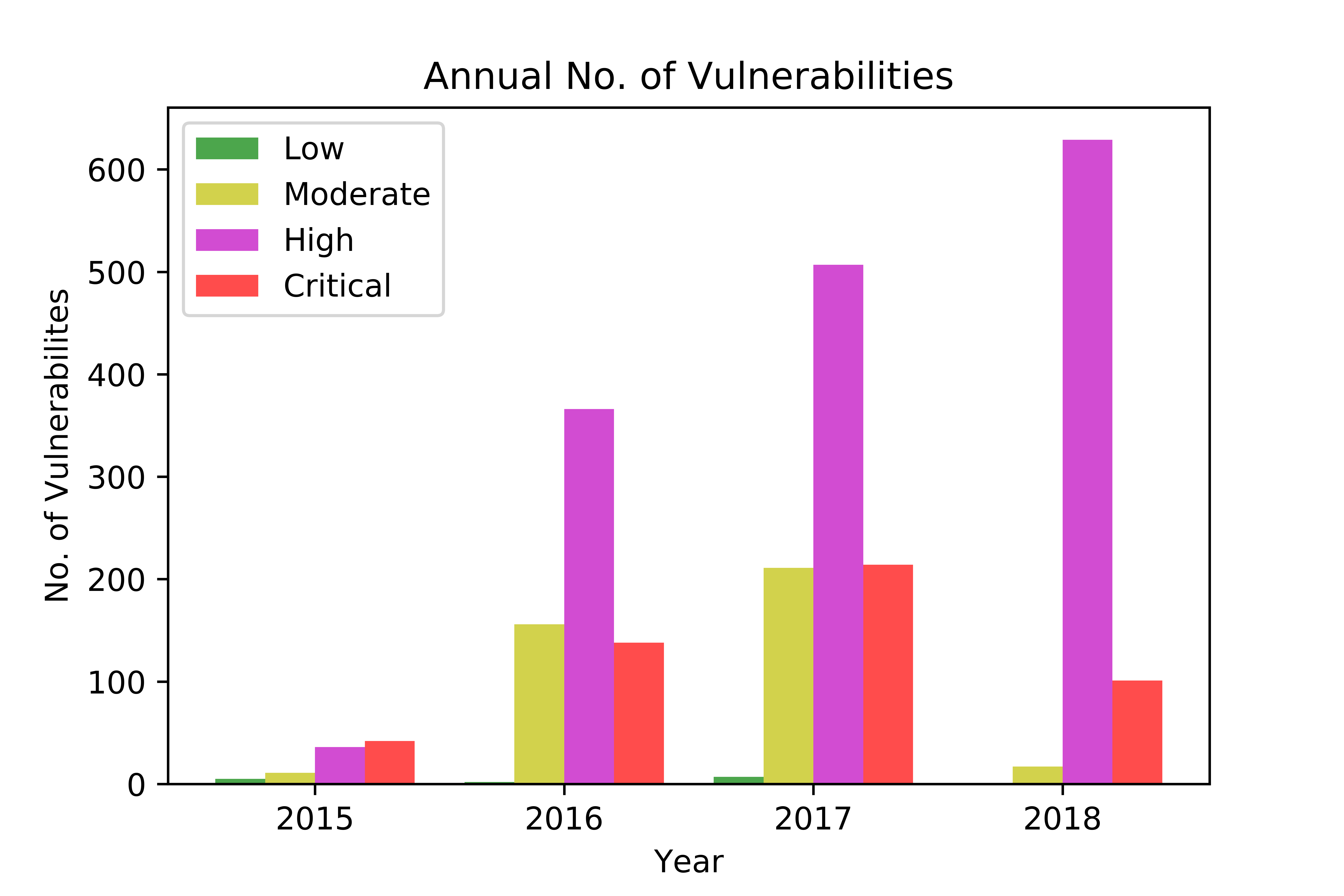
In this paper, we perform a comprehensive study of 2,470 patched Android vulnerabilities that we collect from different data sources such as Android security bulletins, CVEDetails, Qualcomm Code Aurora, AOSP Git repository, and Linux Patchwork. In our data analysis, we focus on determining the affected layers, OS versions, severity levels, and common weakness enumerations (CWE) associated with the patched vulnerabilities. Further, we assess the timeline of each vulnerability, including discovery and patch dates. We find that (i) even though the number of patched vulnerabilities changes considerably from month to month, the relative number of patched vulnerabilities for each severity level remains stable over time, (ii) there is a significant delay in patching vulnerabilities that originate from the Linux community or concern Qualcomm components, even though Linux and Qualcomm provide and release their own patches earlier, (iii) different AOSP versions receive security updates for different periods of time, (iv) for 94% of patched Android vulnerabilities, the date of disclosure in public datasets is not before the patch release date, (v) there exist some inconsistencies among public vulnerability data sources, e.g., some CVE IDs are listed in Android Security bulletins with detailed information, but in CVEDetails they are listed as unknown, (vi) many patched vulnerabilities for newer Android versions likely also affect older versions that do not receive security patches due to end-of-life.
翻译:在本文中,我们全面研究了2,470个补丁和甲状腺脆弱性,我们从诸如安卓安全公告、CveDetails、Qualcomm代码 Aurora、AOSP Git 仓库和Linux Patchwork等不同数据来源收集的2,470个补丁和甲状腺脆弱性。在数据分析中,我们侧重于确定与补丁脆弱性相关的受影响层、OS版本、严重程度和常见弱点计数(CWE),此外,我们评估了每个被补补丁和甲状腺脆弱性的时间表,包括发现和补丁日期。我们发现(一)尽管补补丁脆弱性的数量每月有很大变化,但每个严重程度的补补丁脆弱性相对数量随着时间的推移保持稳定,(二)尽管Linux和Qualcom提供并发布与补丁有关的影响,(三)不同的甲状腺和甲状腺脆弱性得到不同时期的安全更新,(四)对于补丁脆弱性,公共数据集的披露日期并不是在补丁公布日期之前,(五) 也存在一些最新的安全脆弱性。