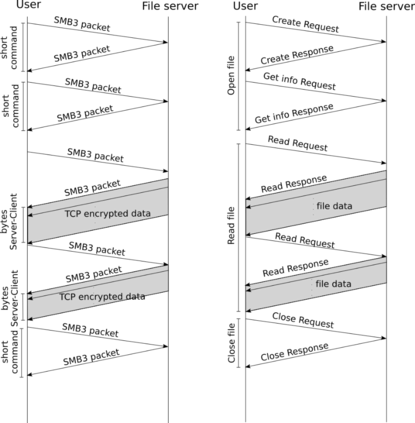
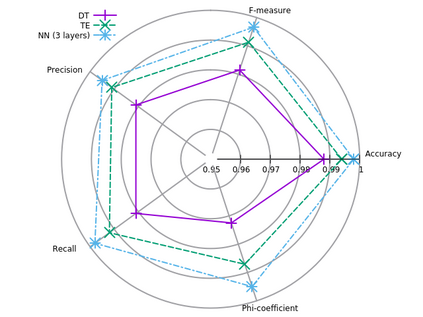
Ransomware is considered as a significant threat for most enterprises since the past few years. In scenarios wherein users can access all files on a shared server, one infected host can lock the access to all shared files. We propose a tool to detect ransomware infection based on file-sharing traffic analysis. The tool monitors the traffic exchanged between the clients and the file servers and using machine learning techniques it searches for patterns in the traffic that betray ransomware actions while reading and overwriting files. The proposal is designed to work for clear text and for encrypted file-sharing protocols. We compare three machine learning models and choose the best for validation. We train and test the detection model using more than 70 ransomware binaries from 26 different strains and more than 2500 hours of not infected traffic from real users. The results reveal that the proposed tool can detect all ransomware binaries, including those not used in training phase (unseen). This paper provides a validation of the algorithm by studying the false positive rate and the amount of information from user files that the ransomware could encrypt before being detected.
翻译:自过去几年以来,Ransomware被视为对大多数企业的重大威胁。在用户可以访问共享服务器上的所有文件的情况下,一个受感染的主机可以锁定所有共享文件的存取权。我们提议了一个基于文件共享交通分析的检测赎金软件感染的工具。该工具监测客户与文件服务器之间的交通往来,并使用机器学习技术搜索交通模式,在阅读和覆盖文件时背叛赎金软件的行动。该提案旨在寻求清晰文本和加密文件共享协议。我们比较了三个机器学习模型,并选择了最佳验证方法。我们用来自26种不同菌株和超过2500小时未受实际用户感染的交通的70多份赎金软件,对检测模型进行了培训和测试。结果显示,拟议工具能够检测所有赎金软件的双边,包括未在培训阶段使用的软件(不见),通过研究假正率和从用户文档获得的信息数量,使赎金软件在被检测之前能够加密,从而验证算法。