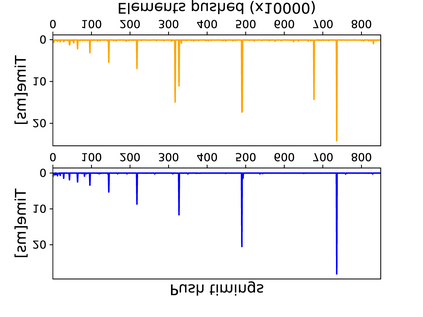
The "eternal war in cache" has reached browsers, with multiple cache-based side-channel attacks and countermeasures being suggested. A common approach for countermeasures is to disable or restrict JavaScript features deemed essential for carrying out attacks. To assess the effectiveness of this approach, in this work we seek to identify those JavaScript features which are essential for carrying out a cache-based attack. We develop a sequence of attacks with progressively decreasing dependency on JavaScript features, culminating in the first browser-based side-channel attack which is constructed entirely from Cascading Style Sheets (CSS) and HTML, and works even when script execution is completely blocked. We then show that avoiding JavaScript features makes our techniques architecturally agnostic, resulting in microarchitectural website fingerprinting attacks that work across hardware platforms including Intel Core, AMD Ryzen, Samsung Exynos, and Apple M1 architectures. As a final contribution, we evaluate our techniques in hardened browser environments including the Tor browser, Deter-Fox (Cao el al., CCS 2017), and Chrome Zero (Schwartz et al., NDSS 2018). We confirm that none of these approaches completely defend against our attacks. We further argue that the protections of Chrome Zero need to be more comprehensively applied, and that the performance and user experience of Chrome Zero will be severely degraded if this approach is taken.
翻译:“ 暗藏中的绝战” 已经到达浏览器, 并提出了多个基于暗藏的侧通道攻击和反措施建议。 一种常见的反措施办法是禁用或限制 JavaScript 被认为对实施袭击至关重要的特征。 为了评估这一方法的有效性, 我们在此工作中力求确定对实施暗藏式袭击至关重要的那些 JavaScript 特征。 我们开发了一系列袭击,逐步减少对 JavaScript 特征的依赖, 其最终结果是第一次基于浏览器的侧通道攻击, 完全由 Cascating Style Ships (CS) 和 HTML (HTML) 构成的退化性能攻击, 甚至当脚本执行完全被屏蔽时, 也在起作用。 然后我们表明, 避免 JavaScript 特征使我们的手法在建筑结构上变得模糊不清, 导致微组织网站识别袭击的特征, 这些硬件平台包括Intel Core, AMRizen, Samsung Exynos, 以及苹果 MM1 建筑。 作为最后的贡献, 我们评估了在更硬化的浏览器环境中环境中的方法, 包括Torbelbelbelbel, Dox (Cx) (CS) (CS) (Ch) 2017) 和Ch) 和Chro 将进一步确认我们的用户攻击的性攻击需要。