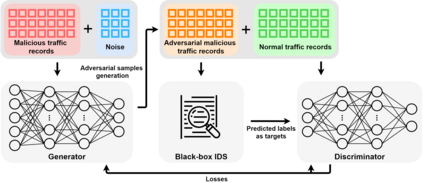
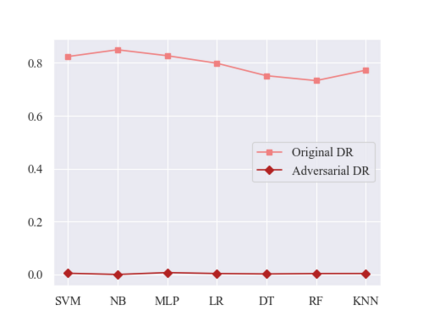
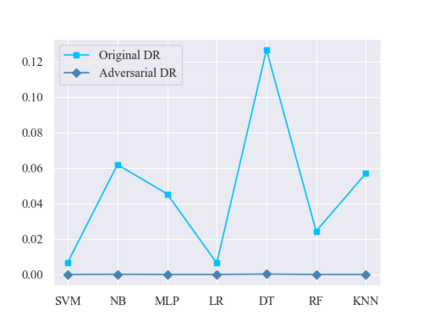
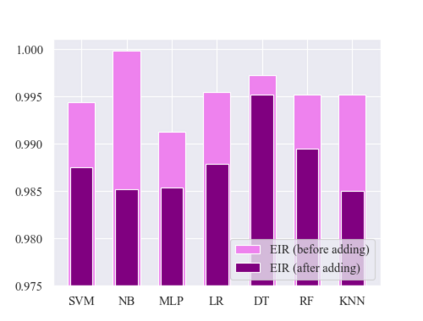
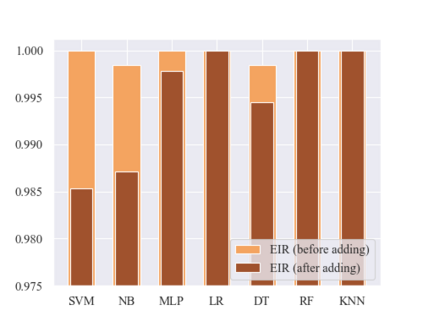
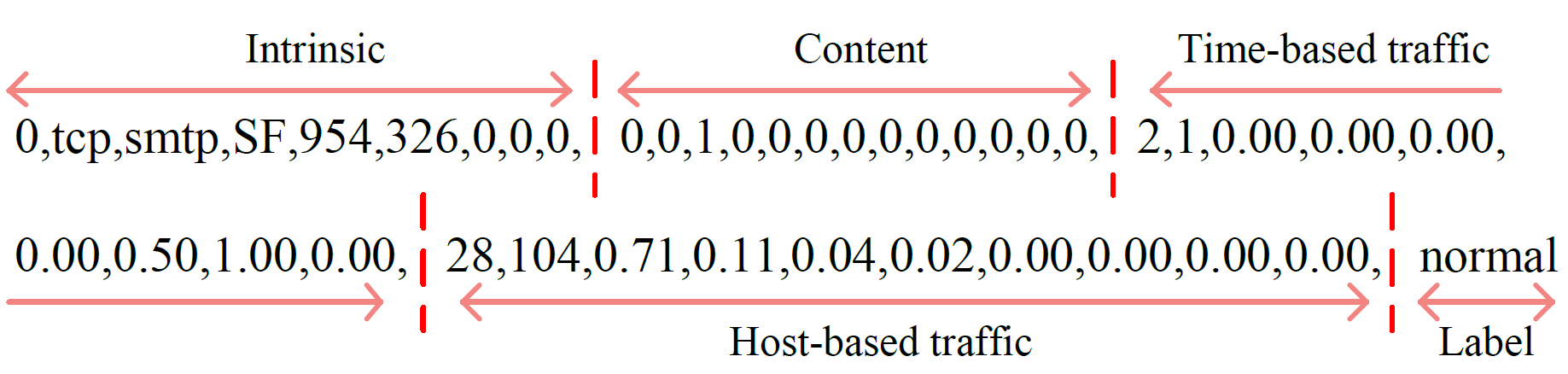
As an important tool in security, the intrusion detection system bears the responsibility of the defense to network attacks performed by malicious traffic. Nowadays, with the help of machine learning algorithms, the intrusion detection system develops rapidly. However, the robustness of this system is questionable when it faces the adversarial attacks. To improve the detection system, more potential attack approaches are under research. In this paper, a framework of the generative adversarial networks, called IDSGAN, is proposed to generate the adversarial malicious traffic records aiming to attack intrusion detection systems by deceiving and evading the detection. Given that the internal structure of the detection system is unknown to attackers, the adversarial attack examples perform the black-box attacks against the detection system. IDSGAN leverages a generator to transform original malicious traffic records into adversarial malicious ones. A discriminator classifies traffic examples and learns the black-box detection system. More significantly, to guarantee the validity of the intrusion, only part of the nonfunctional features are modified in attack traffic. Based on the tests to the dataset NSL-KDD, the feasibility of the model is indicated by attacking multiple kinds of the detection system models with different attack categories, achieving the excellent results. Moreover, the robustness of IDSGAN is verified by changing the amount of the modified features.
翻译:作为安全方面的一个重要工具,入侵探测系统对恶意交通实施的网络攻击负有防御责任。如今,在机器学习算法的帮助下,入侵探测系统迅速发展;然而,当该系统面临对抗性攻击时,其稳健性令人怀疑;为了改进探测系统,正在研究更多潜在的攻击方法;在本文件中,提议一个称为IDSGAN的基因对抗性网络框架,以生成对抗性恶意交通记录,目的是通过欺骗和逃避探测来攻击入侵探测系统。鉴于攻击者不知道探测系统的内部结构,因此,对攻击系统的对抗性攻击实例对探测系统进行黑盒攻击。IDSGAN利用一台发电机将最初的恶意交通记录转换成对抗性恶意攻击系统。一个歧视者对交通进行分类,并学习黑箱探测系统。更重要的是,为了保证入侵的有效性,攻击性交通中只修改了部分不起作用的功能。根据对NSL-KDD的测试,模型的可行性是通过攻击多种类型的探测系统模型对探测系统进行黑盒式攻击,用不同的攻击特征来核查。