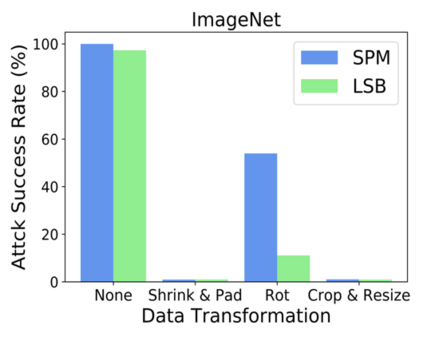
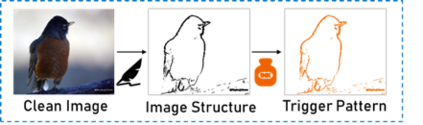
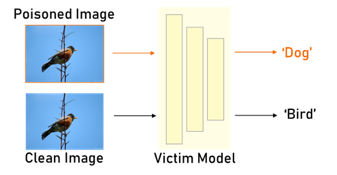
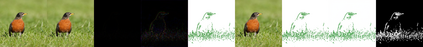
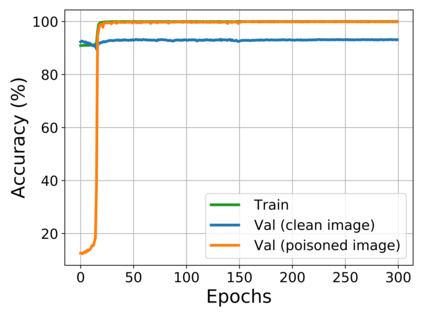
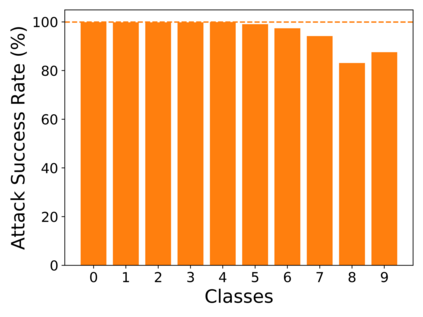
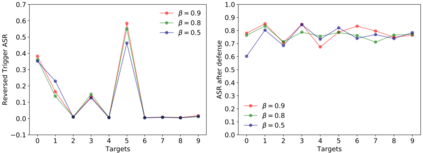
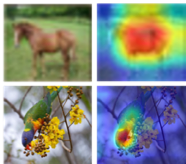
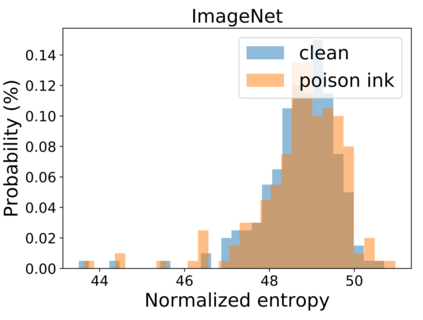
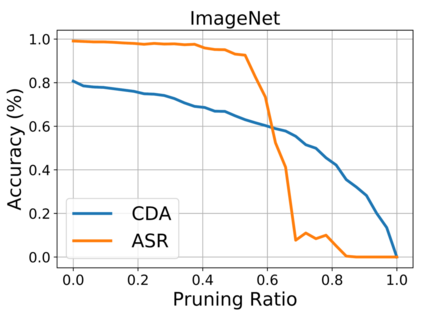
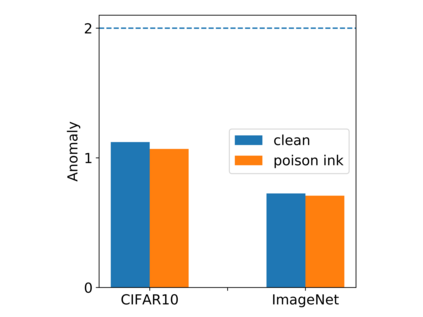
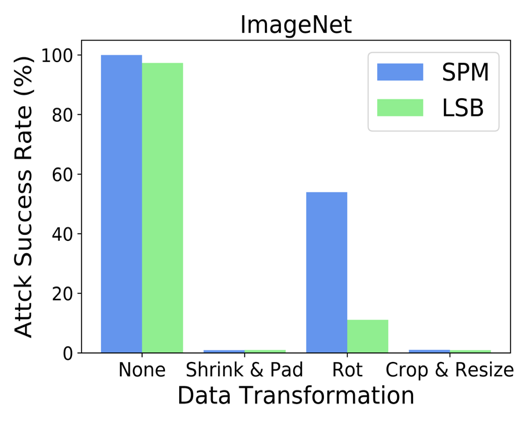
Recent research shows deep neural networks are vulnerable to different types of attacks, such as adversarial attack, data poisoning attack and backdoor attack. Among them, backdoor attack is the most cunning one and can occur in almost every stage of deep learning pipeline. Therefore, backdoor attack has attracted lots of interests from both academia and industry. However, most existing backdoor attack methods are either visible or fragile to some effortless pre-processing such as common data transformations. To address these limitations, we propose a robust and invisible backdoor attack called ``Poison Ink''. Concretely, we first leverage the image structures as target poisoning areas, and fill them with poison ink (information) to generate the trigger pattern. As the image structure can keep its semantic meaning during the data transformation, such trigger pattern is inherently robust to data transformations. Then we leverage a deep injection network to embed such trigger pattern into the cover image to achieve stealthiness. Compared to existing popular backdoor attack methods, Poison Ink outperforms both in stealthiness and robustness. Through extensive experiments, we demonstrate Poison Ink is not only general to different datasets and network architectures, but also flexible for different attack scenarios. Besides, it also has very strong resistance against many state-of-the-art defense techniques.
翻译:最近的研究显示,深层神经网络易受不同类型的攻击,如对抗性攻击、数据中毒攻击和后门攻击。其中,后门攻击是最狡猾的,几乎可在深层次学习管道的每一个阶段发生。因此,后门攻击吸引了学术界和工业界的许多利益。然而,大多数现有的后门攻击方法对于一些不费力的预处理方法(如共同的数据转换)是可见的或脆弱的。为了解决这些限制,我们提议了一种强势和隐形的后门攻击,称为“poison Ink' ”。具体地说,我们首先利用图像结构作为目标中毒区,并用里面的毒药(信息)来制造触发模式。由于图像结构可以在数据转换过程中保持其语义意义,这种触发模式对数据转换具有内在的强大作用。然后我们利用一个深层次的注射网络将这种触发模式嵌入封面图像中,例如共同的数据转换。与现有的流行的后门攻击方法相比,毒性Ink在隐性与坚固性两方面都表现得体。通过广泛的实验,我们证明Teury Ink不仅是普通的,而且是对不同的防御和网络结构的强势。此外也具有很强的防御性。此外,它也具有很强的特性。