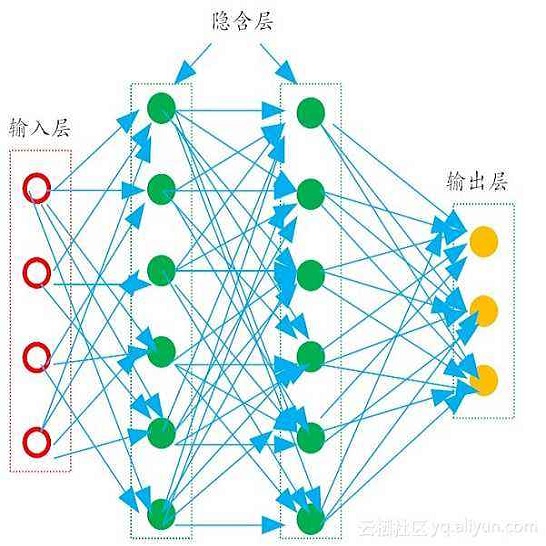
A survey of machine learning techniques trained to detect ransomware is presented. This work builds upon the efforts of Taylor et al. in using sensor-based methods that utilize data collected from built-in instruments like CPU power and temperature monitors to identify encryption activity. Exploratory data analysis (EDA) shows the features most useful from this simulated data are clock speed, temperature, and CPU load. These features are used in training multiple algorithms to determine an optimal detection approach. Performance is evaluated with accuracy, F1 score, and false-negative rate metrics. The Multilayer Perceptron with three hidden layers achieves scores of 97% in accuracy and F1 and robust data preparation. A random forest model produces scores of 93% accuracy and 92% F1, showing that sensor-based detection is currently a viable option to detect even zero-day ransomware attacks before the code fully executes.
翻译:展示了为检测赎金软件而培训的机器学习技术调查,这项工作以泰勒等人利用从CPU动力和温度监测器等内置仪器收集的数据确定加密活动而采用的基于传感器的方法为基础。探索性数据分析(EDA)显示了模拟数据中最有用的特征是时钟速度、温度和CPU负荷。这些特征用于培训多种算法,以确定最佳检测方法。用准确性、F1分和假负率衡量性能。三个隐藏层的多层受控器在准确性方面得分为97%,F1和稳健的数据准备方面得分为97%。随机森林模型得出了93%的准确性分数和92%的F1,表明在代码完全执行之前,基于传感器的检测是目前检测甚至零天赎金软件袭击的可行选择。