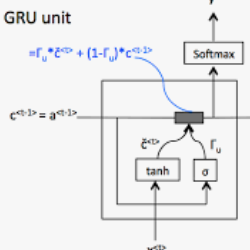
Traditional reactive approach of blacklisting botnets fails to adapt to the rapidly evolving landscape of cyberattacks. An automated and proactive approach to detect and block botnet hosts will immensely benefit the industry. Behavioral analysis of attackers is shown to be effective against a wide variety of attack types. Previous works, however, focus solely on anomalies in network traffic to detect bots and botnet. In this work we take a more robust approach of analyzing the heterogeneous events including network traffic, file download events, SSH logins and chain of commands input by attackers in a compromised host. We have deployed several honeypots to simulate Linux shells and allowed attackers access to the shells. We have collected a large dataset of heterogeneous threat events from the honeypots. We have then combined and modeled the heterogeneous threat data to analyze attacker behavior. Then we have used a deep learning architecture called a Temporal Convolutional Network (TCN) to do sequential and predictive analysis on the data. A prediction accuracy of $85-97\%$ validates our data model as well as our analysis methodology. In this work, we have also developed an automated mechanism to collect and analyze these data. For the automation we have used CYbersecurity information Exchange (CYBEX). Finally, we have compared TCN with Long Short-Term Memory (LSTM) and Gated Recurrent Unit (GRU) and have showed that TCN outperforms LSTM and GRU for the task at hand.
翻译:传统的黑名单肉网被动反应方法未能适应迅速变化的网络攻击环境。一种自动和主动的检测和阻塞肉网主机的方法将极大地有益于该行业。对攻击者的行为分析显示对各种各样的攻击类型有效。然而,以往的工作仅侧重于网络交通中的异常现象,以探测肉网和肉网。在这项工作中,我们采取了一种更强有力的方法,分析各种不同事件,包括网络流量、文件下载事件、SSH登录和攻击者在一个受损主机中输入的命令链。我们部署了几个蜂窝模拟Linux贝壳并允许攻击者接触炮弹。我们从蜂窝收集了大量不同威胁事件的数据集。我们随后将各种威胁数据合并和建模来分析攻击者的行为。然后,我们使用了一个叫作Tental Convolual Convolution 网络(TCN)的深层次学习结构,对数据进行顺序和预测性分析。85-97美元预测精确度验证了我们的数据模型以及我们的分析方法。在这项工作中,我们还开发了一个自动机制,用于收集和分析这些安全的G-I-ILS(我们使用了T-I) 和L-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I-I