比黑客厉害,惠普笔记本存在隐藏键盘记录器
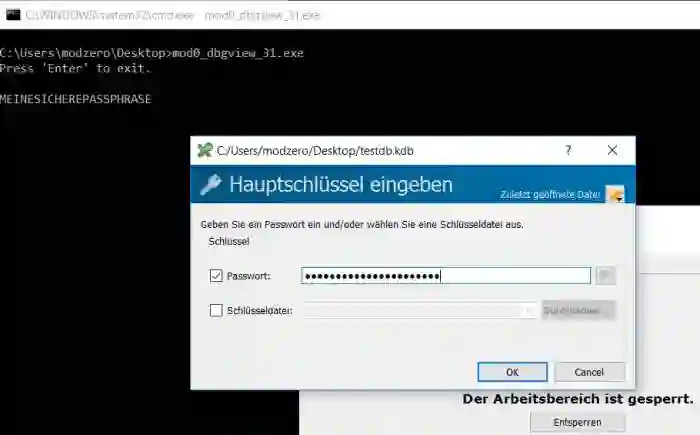
近期,人们都在热议着肆虐全球的“永恒之蓝”勒索蠕虫病毒,感慨着防不胜防的信息安全问题。几乎是在同一时间,来自瑞士安全公司Modzero的安全研究人员指出,全球PC巨头惠普在音频驱动程序中发了一个内置的键盘记录器,可以窥探用户的所有按键输入信息。
该报告称,键盘记录器记录键盘上按下的每个键并记录该信息。然后将信息发送到中央来源。在恶意的情况下,这些信息用于窃取个人资料,如信用卡号码,社会安全号码,密码等等。而该键盘记录软件存在于 Conexant (科胜讯)提供的声卡驱动包里,该驱动包被预装在大量惠普笔记本中。
受影响的型号包括HP Elitebook 800系列、EliteBook Folio G1、HP ProBook 600和400系列等等。详细名单如下所示:
硬件产品型号(S)
HP EliteBook 820 G3 Notebook PC
HP EliteBook 828 G3 Notebook PC
HP EliteBook 840 G3 Notebook PC
HP EliteBook 848 G3 Notebook PC
HP EliteBook 850 G3 Notebook PC
HP ProBook 640 G2 Notebook PC
HP ProBook 650 G2 Notebook PC
HP ProBook 645 G2 Notebook PC
HP ProBook 655 G2 Notebook PC
HP ProBook 450 G3 Notebook PC
HP ProBook 430 G3 Notebook PC
HP ProBook 440 G3 Notebook PC
HP ProBook 446 G3 Notebook PC
HP ProBook 470 G3 Notebook PC
HP ProBook 455 G3 Notebook PC
HP EliteBook 725 G3 Notebook PC
HP EliteBook 745 G3 Notebook PC
HP EliteBook 755 G3 Notebook PC
HP EliteBook 1030 G1 Notebook PC
HP ZBook 15u G3 Mobile Workstation
HP Elite x2 1012 G1 Tablet
HP Elite x2 1012 G1 with Travel Keyboard
HP Elite x2 1012 G1 Advanced Keyboard
HP EliteBook Folio 1040 G3 Notebook PC
HP ZBook 17 G3 Mobile Workstation
HP ZBook 15 G3 Mobile Workstation
HP ZBook Studio G3 Mobile Workstation
HP EliteBook Folio G1 Notebook PC
操作系统(S)
Microsoft Windows 10 32
Microsoft Windows 10 64
Microsoft Windows 10 IOT Enterprise 32-Bit (x86)
Microsoft Windows 10 IOT Enterprise 64-Bit (x86)
Microsoft Windows 7 Enterprise 32 Edition
Microsoft Windows 7 Enterprise 64 Edition
Microsoft Windows 7 Home Basic 32 Edition
Microsoft Windows 7 Home Basic 64 Edition
Microsoft Windows 7 Home Premium 32 Edition
Microsoft Windows 7 Home Premium 64 Edition
Microsoft Windows 7 Professional 32 Edition
Microsoft Windows 7 Professional 64 Edition
Microsoft Windows 7 Starter 32 Edition
Microsoft Windows 7 Ultimate 32 Edition
Microsoft Windows 7 Ultimate 64 Edition
Microsoft Windows Embedded Standard 7 32
Microsoft Windows Embedded Standard 7E 32-Bit
研究人员还告警称“很可能其它使用了Conexant硬件和驱动器的硬件厂商”也受影响。
研究人员还警告称,“可能其它配置了Conexant硬件和驱动程序的硬件供应商”也会受此安全问题影响。
与在国内媒体对此事态度相对平静不同,惠普预装流氓软件事件,国外多家网络媒体发声,引起业内热议(歪果仁确实要比我们信息安全意识高啊!)
按照惠普的解释,作为全球PC巨头,对于2015年就存在的信息安全问题两年后才发现,不免让平实也不太关注个人信息安全的笔者和身边的小伙伴惊呆了。
众所周知,能冠上“中”字头的企业并不多,而中国惠普就是其中一个。中国惠普的由来可自行度娘。
据笔者所知,不少公务员也在用着惠普的PC设备,此次惠普预装流氓软件事件显然没有引起公务员群体和当局的重视,信息隐患细思恐极。不过,笔者了解到,近期某部委下属网络安全和信息化领导小组办公室已经发布公告通报了惠普电脑存在隐藏键盘记录器问题。
MicTray64.exe 1.0.0.46版本进行击键记录的具体过程如下:
int64 keylogger_enable(bool activate)
{
[...]
if ( !keylogger_active )
{
[...]
// 13=WH_KEYBOARD_LL: Installs a hook procedure that
// monitors low-level keyboard input events. For
// more information, see the LowLevelKeyboardProc
// hook procedure.
hKeyloggerHook = SetWindowsHookExW(
13, (HOOKPROC)handle_scancode,
hSelf,
0);
if ( hKeyloggerHook )
{
keylogger_active = 1;
return 0;
}记录功能激活之后,用户每按一次键盘,就会触发以下代码执行:
LRESULT handle_scancode(
int _in_nCode,
WPARAM _in_wParam,
tagKBDLLHOOKSTRUCT *_in_lParam_keystroke)
{
tagKBDLLHOOKSTRUCT *key_stroke;
WPARAM wParam;
int nCode;
int64 target;
DWORD is_keyfoo;
int is_keydown;
char tmp;
int64 key_flags;
int64 key_vk;
key_stroke = _in_lParam_keystroke;
wParam = _in_wParam;
nCode = _in_nCode;
if ( _in_nCode >= 0 )
{
target = (cfg_HotKeyMicScancode >> 8 *
(cfg_HotKeyMicScancode_len - cfg_HotKeyMicScancode_len2));
LODWORD(key_vk) = _in_lParam_keystroke->vkCode;
LODWORD(key_flags) = _in_lParam_keystroke->flags;
is_keyfoo = _in_lParam_keystroke->flags & 1;
is_keydown = ~(key_flags >> 7) & 1;
[*] send_to_dbglog(
0x1D,
L"Mic target 0x%x scancode 0x%x flags 0x%x extra 0x%x vk 0x%x\n",
target,
_in_lParam_keystroke->scanCode,
key_flags,
_in_lParam_keystroke->dwExtraInfo,
key_vk);
conexant_handle_fn_keys(
cfg_MicMuteScancodeSettings,
is_keydown,
key_stroke->scanCode,
target,
&cfg_HotKeyMicScancode_len,
&cfg_HotKeyMicScancode_len2,
1);
if ( cfg_MicMuteScancodeSettings & 4 )
conexant_handle_fn_keys(
cfg_MicMuteScancodeSettings,
is_keydown,
key_stroke->scanCode,
(cfg_HotKeyMicScancode2 >> 8 *
(cfg_HotKeyMicScancode2_len - cfg_HotKeyMicScancode2_len2)),
&cfg_HotKeyMicScancode2_len,
&cfg_HotKeyMicScancode2_len2,
1);
tmp = cfg_SpkMuteScancodeSettings;
if ( cfg_SpkMuteScancodeSettings & 8 && is_keyfoo
|| !(cfg_SpkMuteScancodeSettings & 8) )
{
conexant_handle_fn_keys(
cfg_SpkMuteScancodeSettings,
is_keydown,
key_stroke->scanCode,
(cfg_HotKeySpkScancode >> 8 *
(cfg_HotKeySpkScancode_len - cfg_HotKeySpkScancode_len2)),
&dword_1402709C8,
&dword_1402709CC,
0);
tmp = cfg_SpkMuteScancodeSettings;
}
if ( tmp & 4 && (tmp & 8 && is_keyfoo || !(tmp & 8)) )
conexant_handle_fn_keys(
tmp,
is_keydown,
key_stroke->scanCode,
(cfg_HotKeySpkScancode2 >> 8 *
(cfg_HotKeySpkScancode2_len - cfg_HotKeySpkScancode2_len2)),
&cfg_HotKeySpkScancode2_len,
&cfg_HotKeySpkScancode2_len2,
0);
}
return CallNextHookEx(hhk, nCode, wParam, key_stroke);
} 华盟君只想说,帝国主义亡我之心不死,从英特尔cpu有后门,现在卖给你一个电脑也带键盘记录,网络安全形式严峻,比你我想像的更严重!