42款思科产品或受Apache Struts2远程代码执行漏洞(S2-053)影响
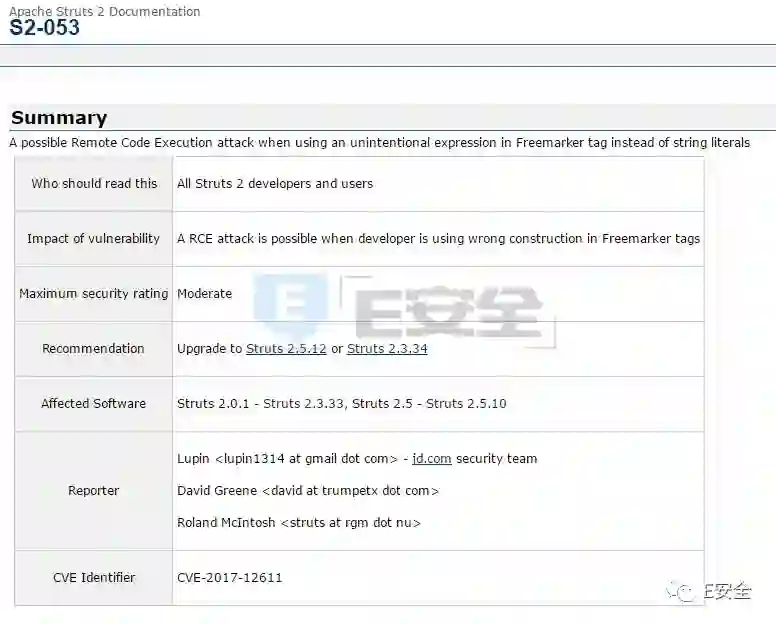
E安全9月12日讯 Apache Struts 9月7日发布安全公告,披露Apache Struts 2存在中危远程代码执行漏洞(S2-053),编号为CVE-2017-12611,当在Freemarker标签中使用表达式常量或强制表达式时使用请求值可能会导致远程代码执行漏洞(见下面的示例)。
在这两种情况下,值属性都使用可写属性,都会受到Freemarker的表达式的影响。
受影响版本
Struts 2.0.1 - Struts 2.3.33, Struts 2.5 - Struts 2.5.10
思科受影响产品列表
与许多厂商一样,思科很久以前就在Web接口上使用了开源Apache Struts。Switchzilla 9月9日宣布42款思科产品或受该漏洞影响。
思科目正在调查协作和网络管理产品、身份服务引擎(Identity Services Engine),一批思科Prime软件、语音和通信、视频和思科网真、以及托管服务等产品。调查的产品包括:
Cisco Unified MeetingPlace
Cisco WebEx Meetings Server
Cisco Data Center Network Manager
Cisco Identity Services Engine (ISE)
Cisco Digital Media Manager
Cisco MXE 3500 Series Media Experience Engines
Cisco Prime Central for Service Providers
Cisco Prime Collaboration Provisioning
Cisco Prime Home
Cisco Prime LAN Management Solution - Solaris
Cisco Prime License Manager
Cisco Prime Network Registrar IP Address Manager (IPAM)
Cisco Prime Network
Cisco Unified Intelligence Center
Cisco Emergency Responder
Cisco Enterprise Chat and Email
Cisco Hosted Collaboration Mediation Fulfillment
Cisco Hosted Collaboration Solution for Contact Center
Cisco Unified Communications Manager IM & Presence Service (formerly CUPS)
Cisco Unified Communications Manager
Cisco Unified Contact Center Enterprise
Cisco Unified E-Mail Interaction Manager
Cisco Unified Intelligent Contact Management Enterprise
Cisco Unified SIP Proxy Software
Cisco Unified Survivable Remote Site Telephony Manager
Cisco Unified Web Interaction Manager
Cisco Unity Connection
Cisco Virtualized Voice Browser
Cisco Enterprise Content Delivery System (ECDS)
Cisco Video Distribution Suite for Internet Streaming (VDS-IS)
Cisco Business Video Services Automation Software
Cisco Cloud Web Security
Cisco Deployment Automation Tool
Cisco Network Device Security Assessment Service
Cisco Network Performance Analysis
Cisco Partner Support Service 1.x
Cisco Prime Service Catalog
Cisco Services Provisioning Platform
Cisco Smart Net Total Care
Cisco Tidal Performance Analyzer
Cisco Unified Service Delivery Platform
Cisco WebEx Network-Based Recording (NBR) Management
思科在公告中指出,一旦调查有进展,思科会发布更新信息,披露受影响的产品。
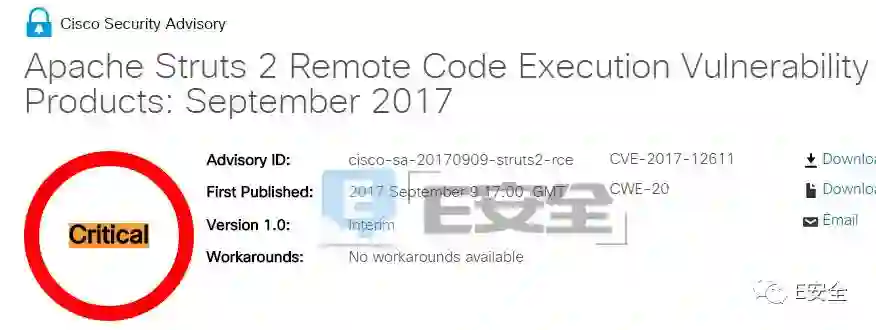
由于远程攻击者可利用该漏洞执行代码,鉴于此,思科在公告中将这个漏洞标记为“Critical”。
思科在公告中表示,一旦识别出易受攻击的产品便会发布公告,并会发布补丁或提出解决方案。
注:本文由E安全编译报道,转载请注明原文地址
https://www.easyaq.com/news/529271046.shtml
相关阅读:
▼点击“阅读原文” 查看更多精彩内容