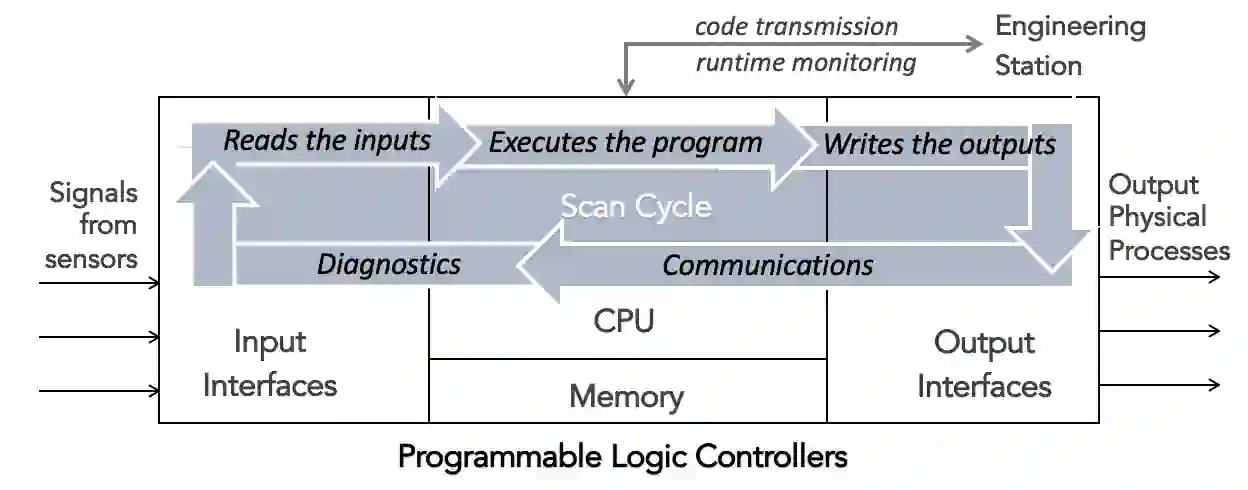
Programmable Logic Controllers (PLCs) play a critical role in the industrial control systems. Vulnerabilities in PLC programs might lead to attacks causing devastating consequences to the critical infrastructure, as shown in Stuxnet and similar attacks. In recent years, we have seen an exponential increase in vulnerabilities reported for PLC control logic. Looking back on past research, we found extensive studies explored control logic modification attacks, as well as formal verification-based security solutions. We performed systematization on these studies, and found attacks that can compromise a full chain of control and evade detection. However, the majority of the formal verification research investigated ad-hoc techniques targeting PLC programs. We discovered challenges in every aspect of formal verification, rising from (1) the ever-expanding attack surface from evolved system design, (2) the real-time constraint during the program execution, and (3) the barrier in security evaluation given proprietary and vendor-specific dependencies on different techniques. Based on the knowledge systematization, we provide a set of recommendations for future research directions, and we highlight the need of defending security issues besides safety issues.
翻译:在工业控制系统中,可编程逻辑控制器(PLC)在工业控制系统中发挥着关键作用。PLC方案中的脆弱性可能导致袭击,如Stuxnet和类似袭击所示,对关键基础设施造成破坏性后果。近年来,我们看到报告的PLC控制逻辑脆弱性呈指数增长趋势。回顾以往的研究,我们发现大量研究探索了控制逻辑改变攻击以及正式的基于核查的安全解决办法。我们对这些研究进行了系统化研究,发现攻击可能损害整个控制和躲避探测链。然而,大多数正式核查研究都对针对PLC程序的特殊技术进行了调查。我们发现,正式核查的每个方面都存在挑战,从(1) 系统设计变化中不断扩大的攻击表面,(2) 方案执行过程中的实时限制,(3) 安全评价的障碍,因为安全评价是专有和具体供应商对不同技术的依赖。基于知识系统化,我们提出了一套关于未来研究方向的建议,我们强调除安全问题之外,还需要捍卫安全问题。