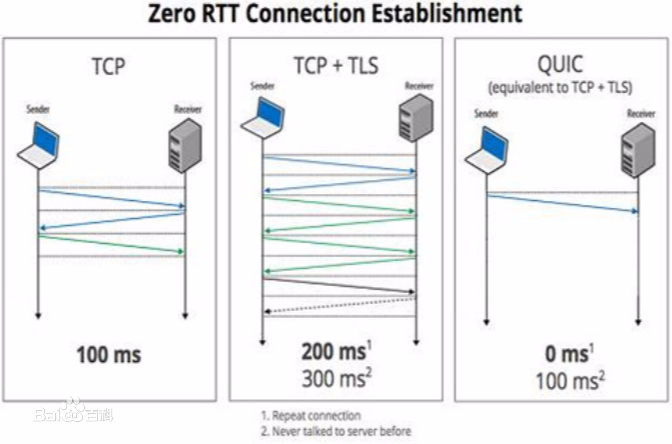
The QUIC protocol is a new approach to combine encryption and transport layer stream abstraction into one protocol to lower latency and improve security. However, the decision to encrypt transport layer functionality may limit the capabilities of firewalls to protect networks. To identify these limitations we created a test environment and analyzed generated QUIC traffic from the viewpoint of a middlebox. This paper shows that QUIC indeed exposes traditional stateful firewalls to UDP hole punching bypass attacks. On the contrary we show the robustness against censorship of QUIC through the encrypted transport layer design and analyze the capabilities to re-gain stateful tracking capabilities by deep packet inspection of the few exposed QUIC header fields.
翻译:QUIC协议是将加密和运输层流抽取纳入一个协议以降低潜伏性并改善安全性的新办法,然而,加密运输层功能的决定可能会限制防火墙保护网络的能力。为了确定这些限制,我们创造了一个测试环境,并从中间框的角度分析了生成的 QUIC 流量。本文显示, QUIC 确实暴露了传统的状态防火墙与UDP 孔相撞的绕行攻击。 相反, 我们通过加密运输层的设计,以及分析通过对少数暴露在QUIC 信头字段进行深封检查以重新获得明确跟踪能力的能力, 来证明对QUIC 的审查是强有力的。