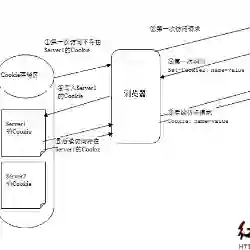
We explore a new type of malicious script attacks: the persistent parasite attack. Persistent parasites are stealthy scripts, which persist for a long time in the browser's cache. We show to infect the caches of victims with parasite scripts via TCP injection. Once the cache is infected, we implement methodologies for propagation of the parasites to other popular domains on the victim client as well as to other caches on the network. We show how to design the parasites so that they stay long time in the victim's cache not restricted to the duration of the user's visit to the web site. We develop covert channels for communication between the attacker and the parasites, which allows the attacker to control which scripts are executed and when, and to exfiltrate private information to the attacker, such as cookies and passwords. We then demonstrate how to leverage the parasites to perform sophisticated attacks, and evaluate the attacks against a range of applications and security mechanisms on popular browsers. Finally we provide recommendations for countermeasures.
翻译:我们探索了一种新型的恶意脚本攻击:持久性寄生虫攻击。 持久性寄生虫是隐性脚本, 在浏览器的缓存中长期存在。 我们通过TCP注射来显示感染受害者缓存的寄生虫脚本。 一旦缓存被感染, 我们实施方法将寄生虫传播到其他广受欢迎的领域, 向受害者客户以及网络上的其他缓存点传播。 我们展示了如何设计寄生虫, 以便寄生虫在受害者的缓存中逗留很长的时间, 不局限于用户访问网站的时间。 我们开发了攻击者与寄生虫之间的秘密通讯渠道, 使攻击者能够控制哪些脚本被执行以及何时执行, 并向攻击者提供私人信息, 例如饼干和密码。 然后我们展示了如何利用寄生虫进行复杂的攻击, 并评估对用户访问网站的一系列应用和安全机制的攻击。 最后, 我们为应对措施提供了建议。