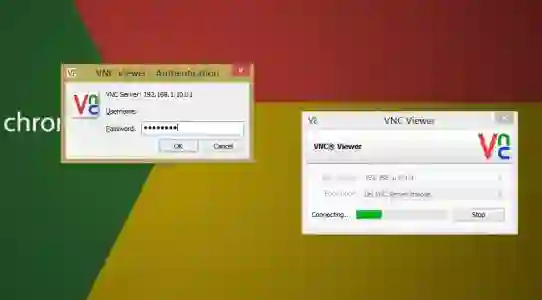
Siemens produce a range of industrial human machine interface (HMI) screens which allow operators to both view information about and control physical processes. For scenarios where an operator cannot physically access the screen, Siemens provide the SM@rtServer features on HMIs, which when activated provides remote access either through their own Sm@rtClient application, or through third party VNC client software. Through analysing this server, we discovered a lack of protection against brute-force password attacks on basic devices. On advanced devices which include a brute-force protection mechanism, we discovered an attacker strategy that is able to evade the mechanism allowing for unlimited password guess attempts with minimal effect on the guess rate. This vulnerability has been assigned two CVEs - CVE-2020-15786 and CVE-2020-157867. In this report, we provide an overview of this vulnerability, discuss the impact of a successful exploitation and propose mitigations to provide protection against this vulnerability. This report accompanies a demo presented at CPSIoTSec 2020.
翻译:Siemens 制作了一系列工业人体机器界面(HMI) 屏幕,使操作者能够查看关于物理过程的信息并控制物理过程。对于操作者无法实际访问屏幕的情形, Siemens 提供HMIs上的 SM@rtServer 功能, 当激活时通过自己的 Sm@rtClient 应用程序或通过第三方 VNC 客户软件提供远程访问。 通过分析这个服务器, 我们发现基本装置缺乏保护, 无法防范粗力密码攻击。 在包括粗力保护机制在内的先进装置上, 我们发现了一个攻击者战略, 能够避开这个机制, 允许无限的密码猜测尝试, 对猜测率影响最小。 这个脆弱性被指定了两个 CVES - CVE-2020-1578 和 CVE-2020-1567 。 我们在本报告中概述了这一脆弱性, 讨论成功开发的影响, 并提出缓解措施, 以防范这种脆弱性。