美国Blackhat2018预览
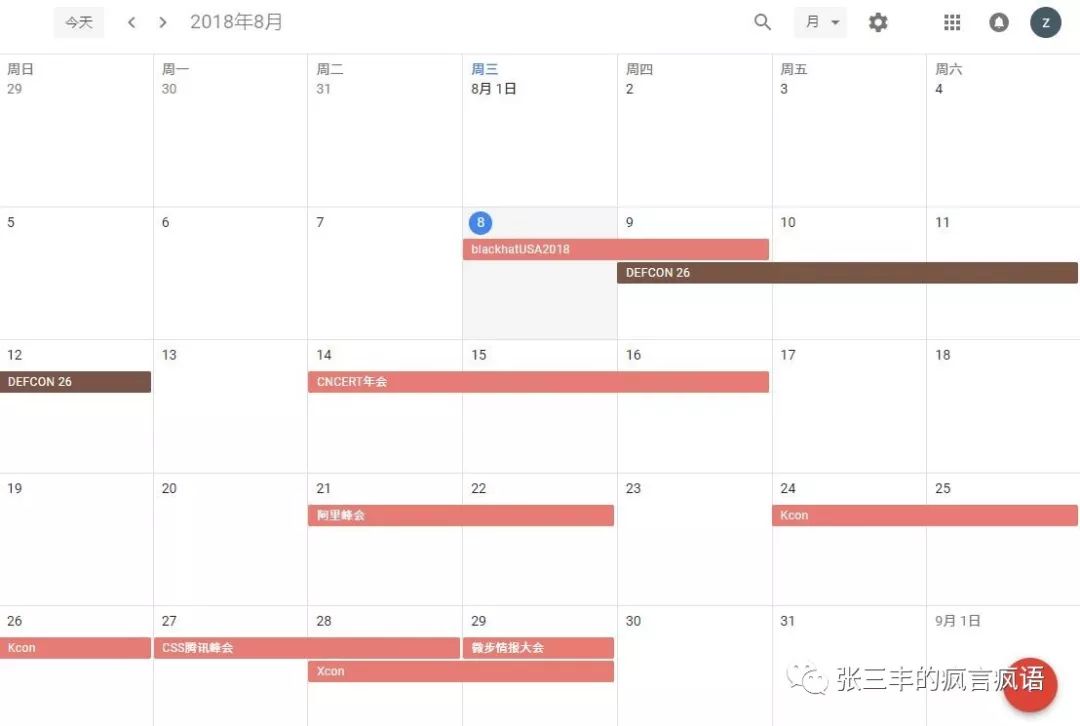
8月属于注定是网络安全的月份,从这周开始安全会议不断,Blackhat、Defcon、CNCERT的年会、阿里网络安全生态会、Kcon、腾讯CSS峰会、Xcon、微步情报大会。可能由于国内的已经够多了,今年似乎没有看到太多blackhat的报道,所以只能靠自己凑合看了下。Blachat会议两天一共118个议题,214个演讲者。过了一遍议题简介第一个感受是黑客的世界仍然保持着无比精彩,安全不仅仅是AI,不仅仅是ML,即便还是Web,二进制这些领域,其研究的要素组件都是前所未有的,科技化使生活的越来越精彩丰富便利,而黑客的眼里这都一片全新的领域而且在其中还游刃有余。另外一个新奇点是,不知道从什么时候开始,竟然多了这么多关注搬砖工程师心理健康的方面的议题。
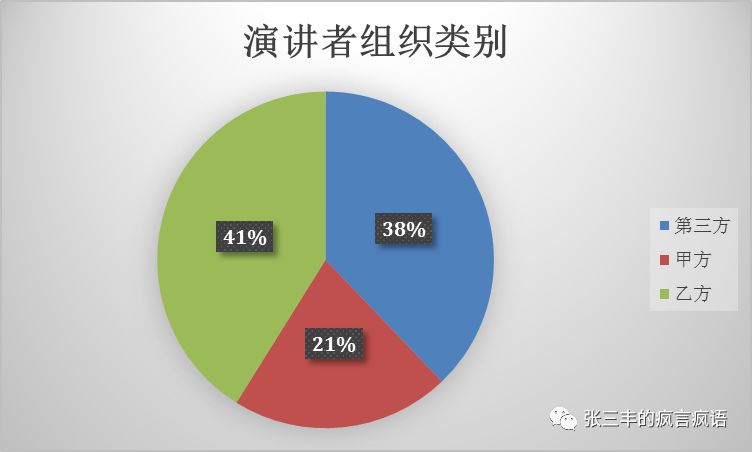
万能的google翻译几乎已经可以大概说明白议题的大概方向了,这里就不一一介绍了。今年特别关注了一下演讲人,这里简单的归为三类,甲方科技巨头、乙方安全公司、第三方组织(政府机构、学校、研究组织、独立研究者等等)
总体来说还是乙方的人数较多,但是出现了很多不同类型的领域的厂商了。如今已经不是清一色的杀毒厂商或者NGFW厂商了。Fireeye似乎也不见了踪影。排除了独立研究人员之后的top10演讲人员组织,可以此了解一下有意思的一些新晋安全厂商或者甲方的最佳实践。
演讲组织 |
演讲人数 |
Microsoft |
10 |
Riscure |
9 |
Tencent Keen Security Lab |
8 |
6 |
|
Graz University of Technology |
6 |
EURECOM |
5 |
IBM Research |
5 |
Duo Security |
4 |
Endgame |
4 |
Global Commission on the Stability of Cyberspace |
4 |
KAIST |
4 |
Positive Technologies |
4 |
其他的乙方公司按演讲顺序简单整理如下,可以感受一下还有剩多少是熟悉的面孔。
VirusBay
Kaspersky
GoSecure
Endgame
Duo Security
Sophos
Riscure
Trail of Bits
Leviathan Security Group
Nozomi Networks
DarkMatter
ZwillGen PLLC
River Loop Security
Eclypsium
PwC
Trimarc
SpecterOps
Immunity Inc
Shostack & Associates
DEVCORE
leveldown security
Cylance Inc
NewAE Technology Inc
Trustwave SpiderLabs
Dragos Inc
Digita Security
Terbium Labs
Cymptom
Positive Technologies
F5 Networks
CrowdStrike Inc
Winsider Seminars & Solutions
Quarkslab
Fleetsmith
Forcepoint
Hex-Rays SA
Lookout
IBM Research
Threatcare
Cisco
NCC Group
G DATA Advanced Analytics
McAfee
IOActive
ForAllSecure
RSM Partners
PortSwigger Web Security
Bastille Networks
Whitescope
QED
HORNE Cyber
Secarma Ltd
Red Sky Solutions,LLC
RSA Security
Tripwire VERT
时间仓促就未对厂商类型再做进一步分类分析了。最后附上议题,供各位与会者参考一下,同一个时间段有上10个议题,也就只能选一个方向听一下了。
Keynote |
Optimistic Dissatisfaction with the Status Quo: Steps We Must Take to Improve Security in Complex Landscapes |
WEDNESDAY | 9:00AM |
AWS上检测凭证被窃 |
Detecting Credential Compromise in AWS |
WEDNESDAY | 10:30AM |
识别online scanners |
Dissecting Non-Malicious Artifacts: One IP at a Time |
WEDNESDAY | 10:30AM |
ESI引擎漏洞挖掘 |
Edge Side Include Injection: Abusing Caching Servers into SSRF and Transparent Session Hijacking |
WEDNESDAY | 10:30AM |
钓鱼邮件安全意识 |
Exposing the Bait: A Qualitative Look at the Impact of Autonomous Peer Communication to Enhance Organizational Phishing Detection |
WEDNESDAY | 10:30AM |
Xori自动反编译分析恶意软件 |
Finding Xori: Malware Analysis Triage with Automated Disassembly |
WEDNESDAY | 10:30AM |
安全从业人员人文关怀 |
Holding on for Tonight: Addiction in InfoSec |
WEDNESDAY | 10:30AM |
SBOM物联网政策 |
How I Learned to Stop Worrying and Love the SBOM |
WEDNESDAY | 10:30AM |
恶意软件检测 |
Measuring the Speed of the Red Queen's Race; Adaption and Evasion in Malware |
WEDNESDAY | 10:30AM |
硬件钱包 |
Software Attacks on Hardware Wallets |
WEDNESDAY | 10:30AM |
Hyper-V漏洞挖掘 |
A Dive in to Hyper-V Architecture & Vulnerabilities |
WEDNESDAY | 11:15AM |
以太坊智能合约区块链漏洞挖掘 |
Blockchain Autopsies - Analyzing Ethereum Smart Contract Deaths |
WEDNESDAY | 11:15AM |
深度学习神经网络做安全检测 |
Deep Neural Networks for Hackers: Methods, Applications, and Open Source Tools |
WEDNESDAY | 11:15AM |
机器人的法律探讨 |
From Bot to Robot: How Abilities and Law Change with Physicality |
WEDNESDAY | 11:15AM |
Keen team的iOS越狱 |
KeenLab iOS Jailbreak Internals: Userland Read-Only Memory can be Dangerous |
WEDNESDAY | 11:15AM |
Miasm工程框架 |
Miasm: Reverse Engineering Framework |
WEDNESDAY | 11:15AM |
JavaScript引擎内置的即时(JIT)编译器漏洞挖掘 |
New Trends in Browser Exploitation: Attacking Client-Side JIT Compilers |
WEDNESDAY | 11:15AM |
黑客与压力 |
Stress and Hacking: Understanding Cognitive Stress in Tactical Cyber Ops |
WEDNESDAY | 11:15AM |
TRITON工控 |
TRITON: How it Disrupted Safety Systems and Changed the Threat Landscape of Industrial Control Systems, Forever |
WEDNESDAY | 11:15AM |
软件定义SD-WAN攻击 |
CANCELLED: Too Soft[ware Defined] Networks: SD-WAN VulnerabilityAssessment |
WEDNESDAY | 1:30PM |
VPN攻击 |
Compression Oracle Attacks on VPN Networks |
WEDNESDAY | 1:30PM |
ICS防火墙 |
Deep Dive into an ICS Firewall, Looking for the Fire Hole |
WEDNESDAY | 1:30PM |
法律政策 |
Legal Landmines: How Law and Policy are Rapidly Shaping Information Security |
WEDNESDAY | 1:30PM |
地缘政治与恶意软件分析 |
No Royal Road … Notes on Dangerous Game |
WEDNESDAY | 1:30PM |
UEFI firmware固件攻击 |
Remotely Attacking System Firmware |
WEDNESDAY | 1:30PM |
无线SD卡攻击 |
Reversing a Japanese Wireless SD Card - From Zero to Code Execution |
WEDNESDAY | 1:30PM |
侧信道攻击解密 |
Screaming Channels: When Electromagnetic Side Channels Meet Radio Transceivers |
WEDNESDAY | 1:30PM |
汽车固件ECU攻击 |
There will be Glitches: Extracting and Analyzing Automotive Firmware Efficiently |
WEDNESDAY | 1:30PM |
检测twitter机器人 |
Don't @ Me: Hunting Twitter Bots at Scale |
WEDNESDAY | 2:40PM |
ROSE远程在线社工 |
Every ROSE has its Thorn: The Dark Art of Remote Online Social Engineering |
WEDNESDAY | 2:40PM |
工作站到域控的攻击 |
From Workstation to Domain Admin: Why Secure Administration isn't Secure and How to Fix it |
WEDNESDAY | 2:40PM |
Meltdown详解 |
Meltdown: Basics, Details, Consequences |
WEDNESDAY | 2:40PM |
黑客的心理健康 |
Mental Health Hacks: Fighting Burnout, Depression and Suicide in the Hacker Community |
WEDNESDAY | 2:40PM |
Sysmon高级玩法 |
Subverting Sysmon: Application of a Formalized Security Product Evasion Methodology |
WEDNESDAY | 2:40PM |
BMC攻击 |
The Unbearable Lightness of BMC's |
WEDNESDAY | 2:40PM |
威胁建模 |
Threat Modeling in 2018: Attacks, Impacts and Other Updates |
WEDNESDAY | 2:40PM |
WireGuard密码学攻击VPN |
WireGuard: Next Generation Secure Network Tunnel |
WEDNESDAY | 2:40PM |
iOS 11的async_wake漏洞利用 |
A Brief History of Mitigation: The Path to EL1 in iOS 11 |
WEDNESDAY | 4:00PM |
Meltdown漏洞响应的背后故事 |
Behind the Speculative Curtain: The True Story of Fighting Meltdown and Spectre |
WEDNESDAY | 4:00PM |
新型web攻击面path normalization漏洞挖掘 |
Breaking Parser Logic: Take Your Path Normalization off and Pop 0days Out! |
WEDNESDAY | 4:00PM |
工控网关漏洞 |
Breaking the IIoT: Hacking industrial Control Gateways |
WEDNESDAY | 4:00PM |
LET网络注入恶意包 |
LTE Network Automation Under Threat |
WEDNESDAY | 4:00PM |
针对用于移动和物联网设备的微软Cortana攻击 |
Open Sesame: Picking Locks with Cortana |
WEDNESDAY | 4:00PM |
GO语言漏洞 |
Squeezing a Key through a Carry Bit |
WEDNESDAY | 4:00PM |
X86架构下的提取漏洞 |
Why so Spurious? How a Highly Error-Prone x86/x64 CPU "Feature" can be Abused to Achieve Local Privilege Escalation on Many Operating Systems |
WEDNESDAY | 4:00PM |
零信任网络的威胁 |
ZEROing Trust: Do Zero Trust Approaches Deliver Real Security? |
WEDNESDAY | 4:00PM |
AFL的盲点 |
AFL's Blindspot and How to Resist AFL Fuzzing for Arbitrary ELF Binaries |
WEDNESDAY | 5:05PM |
加密货币IOTA的攻击 |
A Tangled Curl: Attacks on the Curl-P Hash Function Leading to Signature Forgeries in the IOTA Signature Scheme |
WEDNESDAY | 5:05PM |
KVM Hypervisor安全设计 |
Back to the Future: A Radical Insecure Design of KVM on ARM |
WEDNESDAY | 5:05PM |
区块链分散和抗删除的域名技术对抗 |
Beating the Blockchain by Mapping Out Decentralized Namecoin and Emercoin Infrastructure |
WEDNESDAY | 5:05PM |
安全社区的X骚扰事件 |
How can Communities Move Forward After Incidents of Sexual Harassment or Assault? |
WEDNESDAY | 5:05PM |
开源工具ChipWhisperer-Lint在硬件侧信到攻击中使用 |
I, for One, Welcome Our New Power Analysis Overlords |
WEDNESDAY | 5:05PM |
腐败对信息安全社区的影响 |
InfoSec Philosophies for the Corrupt Economy |
WEDNESDAY | 5:05PM |
黑手党是否接管了网络犯罪 |
Is the Mafia Taking Over Cybercrime? |
WEDNESDAY | 5:05PM |
针对物理隔离Air-Gap的攻击 |
The Air-Gap Jumpers |
WEDNESDAY | 5:05PM |
安卓ARTist逆向分析工具 |
ARTist - A Novel Instrumentation Framework for Reversing and Analyzing Android Apps and the Middleware |
THURSDAY | 9:00AM |
网络安全的PTSD创伤后应激障碍 |
Demystifying PTSD in the Cybersecurity Environment |
THURSDAY | 9:00AM |
基于主机的Mac OS防火墙研究 |
Fire & Ice: Making and Breaking macOS Firewalls |
THURSDAY | 9:00AM |
WinVote Voting Machines必胜投票机取证 |
Lessons from Virginia - A Comparative Forensic Analysis of WinVote Voting Machines |
THURSDAY | 9:00AM |
用网上情报资源预测支付欺诈 |
Money-rity Report: Using Intelligence to Predict the Next Payment Card Fraud Victims |
THURSDAY | 9:00AM |
deception欺骗检测技术的弱点 |
Real Eyes, Realize, Real Lies: Beating Deception Technologies |
THURSDAY | 9:00AM |
BlackBerry产品安全管理经验 |
Stop that Release, There's a Vulnerability! |
THURSDAY | 9:00AM |
WebAssembly漏洞挖掘 |
The Problems and Promise of WebAssembly |
THURSDAY | 9:00AM |
YubiKey双因子 |
Two-Factor Authentication, Usable or Not? A Two-Phase Usability Study of the FIDO U2F Security Key |
THURSDAY | 9:00AM |
ATM机攻击设备 |
Black Box is Dead. Long Live Black Box! |
THURSDAY | 9:45AM |
SSO SAML漏洞挖掘 |
Identity Theft: Attacks on SSO Systems |
THURSDAY | 9:45AM |
内核攻击 |
Kernel Mode Threats and Practical Defenses |
THURSDAY | 9:45AM |
网络安全外交 |
New Norms and Policies in Cyber-Diplomacy |
THURSDAY | 9:45AM |
VSS备份特性攻击 |
Reconstruct the World from Vanished Shadow: Recovering Deleted VSS Snapshots |
THURSDAY | 9:45AM |
iot领域蜂窝设备的漏洞挖掘 |
Snooping on Cellular Gateways and Their Critical Role in ICS |
THURSDAY | 9:45AM |
女网络安全工程师的招聘 |
The Science of Hiring and Retaining Female Cybersecurity Engineers |
THURSDAY | 9:45AM |
针对Windows Notification的攻击 |
The Windows Notification Facility: Peeling the Onion of the Most Undocumented Kernel Attack Surface Yet |
THURSDAY | 9:45AM |
构造语音认证攻击 |
Your Voice is My Passport |
THURSDAY | 9:45AM |
macOS MDM安全 |
A Deep Dive into macOS MDM (and How it can be Compromised) |
THURSDAY | 11:00AM |
对机器学习算法的攻击 |
AI & ML in Cyber Security - Why Algorithms are Dangerous |
THURSDAY | 11:00AM |
交易安全Trading Stocks |
Are You Trading Stocks Securely? Exposing Security Flaws in Trading Technologies |
THURSDAY | 11:00AM |
微码安全研究 |
Decompiler Internals: Microcode |
THURSDAY | 11:00AM |
检测恶意云账号行为 |
Detecting Malicious Cloud Account Behavior: A Look at the New Native Platform Capabilities |
THURSDAY | 11:00AM |
针对OpenPGP and S/MIME攻击 |
Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels |
THURSDAY | 11:00AM |
x86处理器的硬件后门 |
GOD MODE UNLOCKED - Hardware Backdoors in x86 CPUs |
THURSDAY | 11:00AM |
医疗领域hl7协议漏洞挖掘 |
Pestilential Protocol: How Unsecure HL7 Messages Threaten Patient Lives |
THURSDAY | 11:00AM |
移动端的监听技术 |
Stealth Mango and the Prevalence of Mobile Surveillanceware |
THURSDAY | 11:00AM |
自动驾驶的安全 |
Applied Self-Driving Car Security |
THURSDAY | 12:10PM |
视频水印的攻击 |
None of My Pixel is Your Business: Active Watermarking Cancellation Against Video Streaming Service |
THURSDAY | 12:10PM |
智慧城市的漏洞挖掘 |
Outsmarting the Smart City |
THURSDAY | 12:10PM |
TLS 1.3安全 |
Playback: A TLS 1.3 Story |
THURSDAY | 12:10PM |
增强机器学习抗攻击能力 |
Protecting the Protector, Hardening Machine Learning Defenses Against Adversarial Attacks |
THURSDAY | 12:10PM |
域控攻击 |
So I became a Domain Controller |
THURSDAY | 12:10PM |
TLB的侧信道攻击 |
TLBleed: When Protecting Your CPU Caches is Not Enough |
THURSDAY | 12:10PM |
WebAssembly漏洞挖掘 |
WebAssembly: A New World of Native Exploits on the Browser |
THURSDAY | 12:10PM |
缓解speculative漏洞的故事 |
Wrangling with the Ghost: An Inside Story of Mitigating Speculative Execution Side Channel Vulnerabilities |
THURSDAY | 12:10PM |
关于DRAM的漏洞Rowhammer |
Another Flip in the Row |
THURSDAY | 2:30PM |
反序列化漏洞自动发现 |
Automated Discovery of Deserialization Gadget Chains |
THURSDAY | 2:30PM |
社工攻击研究 |
Catch me, Yes we can! – Pwning Social Engineers using Natural Language Processing Techniques in Real-Time |
THURSDAY | 2:30PM |
智能手机baseband攻击 |
Exploitation of a Modern Smartphone Baseband |
THURSDAY | 2:30PM |
自动漏洞利用(内核) |
From Thousands of Hours to a Couple of Minutes: Automating Exploit Generation for Arbitrary Types of Kernel Vulnerabilities |
THURSDAY | 2:30PM |
Autism Spectrum Disorder研究 |
How can Someone with Autism Specifically Enhance the Cyber Security Workforce? |
THURSDAY | 2:30PM |
SATCOM安全研究 |
Last Call for SATCOM Security |
THURSDAY | 2:30PM |
iot漏洞的合法责任 |
Legal Liability for IOT Cybersecurity Vulnerabilities |
THURSDAY | 2:30PM |
widnows Defender的仿真器 |
Windows Offender: Reverse Engineering Windows Defender's Antivirus Emulator |
THURSDAY | 3:50PM |
mPOSl漏洞挖掘 |
For the Love of Money: Finding and Exploiting Vulnerabilities in Mobile Point of Sales Systems |
THURSDAY | 3:50PM |
微软OSR团队对Hyper-V漏洞的挖掘 |
Hardening Hyper-V through Offensive Security Research |
THURSDAY | 3:50PM |
IoT恶意软件的综合调查分析框架 |
IoT Malware: Comprehensive Survey, Analysis Framework and Case Studies |
THURSDAY | 3:50PM |
通过深度学习来帮助侧信道攻击 |
Lowering the Bar: Deep Learning for Side Channel Analysis |
THURSDAY | 3:50PM |
大型机漏洞挖掘 |
Mainframe [z/OS] Reverse Engineering and Exploit Development |
THURSDAY | 3:50PM |
web缓存中毒攻击 |
Practical Web Cache Poisoning: Redefining 'Unexploitable' |
THURSDAY | 3:50PM |
小型组织创建SDL的实践 |
SDL That Won't Break the Bank |
THURSDAY | 3:50PM |
无线电紧急系统的攻击 |
SirenJack: Cracking a 'Secure' Emergency Warning Siren System |
THURSDAY | 3:50PM |
植入式医疗设备的漏洞挖掘 |
Understanding and Exploiting Implanted Medical Devices |
THURSDAY | 3:50PM |
docker攻击 |
An Attacker Looks at Docker: Approaching Multi-Container Applications |
THURSDAY | 5:00PM |
IBM的AI攻击DeepLocker研究DeepLocker - Concealing Targeted Attacks with AI Locksmithing |
DeepLocker - Concealing Targeted Attacks with AI Locksmithing |
THURSDAY | 5:00PM |
模糊测试Fuzz研究 |
Follow the White Rabbit: Simplifying Fuzz Testing Using FuzzExMachina |
THURSDAY | 5:00PM |
PHP的非序列漏洞研究 |
It's a PHP Unserialization Vulnerability Jim |
THURSDAY | 5:00PM |
NOC BH统计分析报告 |
Lessons and Lulz: The 4th Annual Black Hat USA NOC Report |
THURSDAY | 5:00PM |
NOC报告 |
Lessons and Lulz: The 4th Annual Black Hat USA NOC Report |
THURSDAY | 5:00PM |
Keen team对特斯拉攻击的分享 |
Over-the-Air: How we Remotely Compromised the Gateway, BCM, and Autopilot ECUs of Tesla Cars |
THURSDAY | 5:00PM |
TLS漏洞分析 |
Return of Bleichenbacher's Oracle Threat (ROBOT) |
THURSDAY | 5:00PM |
SDN的渗透测试框架 |
The Finest Penetration Testing Framework for Software-Defined Networks |
THURSDAY | 5:00PM |
移动恶意软件攻击技术分析 |
Unpacking the Packed Unpacker: Reverse Engineering an Android Anti-Analysis Native Library |
THURSDAY | 5:00PM |